Blockchain security: An in-depth look at smart contract audits

As the blockchain industry evolves, one of the most fascinating and potentially transformational innovations is the concept of smart contracts. Functioning as self-operating programs, smart contracts can execute transactions without the need for an intermediary, thereby increasing efficiencies and reducing costs.
However, the automated and immutable nature of smart contracts brings with it a certain level of risk. The protocols are often responsible for managing and transferring high-value assets, which makes security anything but an afterthought. In this decentralized landscape, ensuring smart contract security is paramount, and one of the most effective ways to achieve this is through a thorough smart contract security audit.
In the following sections, we’ll venture deeper into what smart contract security audits are, the role they play in enhancing smart contract reliability, and why they are now an indispensable step in the smart contract deployment journey.
What is a smart contract security audit?
A term that perhaps sounds complex on first encounter, ‘smart contract security audit’, is relatively straightforward once unpacked. It is a rigorous, detailed examination carried out on a protocol’s smart contract code to detect potential security flaws, inefficient coding practices, and to suggest appropriate solutions to rectify the detected weaknesses. This pivotal process plays a substantial role in assuring the security, reliability, and performance of today’s revolutionary decentralized applications on Web3 platforms.
During this critical audit, security experts run a fine-toothed comb through essential aspects of the application, including its code, logic, architectural design, and security strategies. The objective is to catch any potential vulnerabilities that could be the prey of malicious actors and identify possible areas for improvement. Tools of both automated and manual nature are employed in this process.
In the realm of decentralized applications, vulnerabilities can have catastrophic consequences. This is why security audits are mandatory before launching or updating an application. The blockchain, whether it be Ethereum, Avalanche, or BNB Chain, is open for anyone to interact with – from end-users to attackers looking for exploitable vulnerabilities.
An audit concludes with the release of a detailed review report. This document outlines their findings, the measures taken for resolution, and any other issues, coupled with a roadmap for tackling unresolved ones. Armed with this comprehensive audit report, project developers can confidently deploy their smart contracts, secure in the knowledge that the infrastructure is securely built, and user funds are adequately protected.
Why smart contract security audits?
The exponential surge in blockchain technology applications has brought smart contract security issues into sharp focus. For the uninitiated, smart contracts are simply computer programs that automatically execute transactions when predetermined conditions are met.
While this forward-thinking technology has brought about an unprecedented level of efficiency, it also brings on board certain risks with it. This is where the role of smart contract security audits becomes crucial.
Why, you might ask? Well, let’s first understand the repercussions of neglecting smart contract security audits. Minor coding errors, overlooked due to the absence of proper audits, can quickly escalate into major security breaches, resulting in large-scale asset heists.
A chilling run-down memory lane brings us to the DAO hack on the Ethereum blockchain, which led to a loss of around $60 million in Ether. This event shook the cryptocurrency industry, underlining the critical importance of an impregnable security infrastructure.

Businesses are well aware of the irreversible and autonomous nature of smart contracts, prompting a well-founded degree of caution towards their deployment. The inability to change or modify smart contracts after deployment, backed with the inherent security vulnerabilities, risk not only loss of the contract but its associated assets as well.
Therefore, smart contract security auditing is no longer an optional add-on, but a critical necessity, driven by several compelling reasons:
- Avoidance of costly errors: Identifying and rectifying errors early in the development lifecycle can prevent catastrophic failures post-launch.
- Expert review: Automated algorithms can detect a host of issues, but nothing beats the precision of a seasoned security auditor manually checking the code to eliminate false positives.
- Thwarting security attacks: Awareness and timely action on security vulnerabilities can potentially ward off malicious attacks.
- Assurance of security: Stakeholders of decentralized products gain confidence in the solidity of the code underpinning their applications.
- Ensuring continuous security assessment: The smart contract auditing procedure facilitates continuous security assessments, helping developers constantly improve their application’s security infrastructure.
- Provision of comprehensive reports: Audit reports offer a wealth of information, including a bird’s-eye view of your application’s security status, detailed vulnerability explanations, and recommendations for risk mitigation.
Common smart contract vulnerabilities
Smart contracts, while revolutionary, can be riddled with pitfalls if not coded and tested carefully. One of the main advantages of a thorough audit is the ability to identify common and potential vulnerabilities before smart contracts are deployed into the public blockchain. Here are some of the common vulnerabilities often found in smart contract security audits:
- Reentrancy issues: This type of attack occurs when a smart contract function is being called, and during the execution of that function, control is transferred to an external untrusted contract which comes back to the original contract and runs the same function again. This recursive calling can lead to repetitive withdrawals, potentially draining funds from the contract.
- Integer overflow and underflow: These issues arise when arithmetic operations generate a result exceeding the maximum or minimum size that can be held within a variable. The overflow or underflow results in incorrect values being returned and used, leading to potential exploitation.
- Frontrunning opportunities: Frontrunning in smart contracts refers to the ability of an attacker to see a smart contract interaction request and then craft a proposal that, by paying a higher gas fee, gets placed ahead of the original request. This exploitation can lead to financial losses for the original requester or an unfair advantage to the attacker.
- Replay attack: Replay attacks are devious; they involve the capturing and retransmission of a valid data transmission. They can occur during blockchain hard fork events, causing messages on the new network to be used maliciously to extract funds from the old network.
- Function visibility errors: Function visibility defines who can call a program’s function. By default, functions are public in Solidity. Therefore, if not explicitly set, functions that were intended to be private could be called by anyone—potentially enabling unauthorized operations.
- Centralization risks: The beauty of blockchain lies in its decentralized nature. However, if smart contracts retain some types of central control, it introduces a point of failure that could be exploited, undermining the entire security framework.
- Unlocked compiler version: Different compiler versions can lead to different bytecode, leading to unintended complications. Smart contracts should lock the version of the compiler they use to maintain consistency.
Understanding these common vulnerabilities is an essential step towards ensuring the robustness of smart contracts, enabling them to withstand potential attacks and exploits.
Mitigating risks: Solutions and strategies
Navigating the landscape of smart contract development and deployment comes with inherent risks. However, smart contract security audits act as your compass, identifying potential issues and charting a roadmap towards more secure implementation. Here are some strategies for mitigating risks and enhancing the strength of your smart contracts:
- Regular security audits: Regular security auditing is key in maintaining continual assessment and assurance of smart contract security. Audits should not be a one-time process but a repeat activity incorporated into the development lifecycle.
- Adopting industry best practices: Best practices provide developers with benchmarks for their coding methodologies. They include coding strategies and resources that have been proven to create safe and efficient smart contracts.
- Security testing: From conducting fuzzing (inputting massive amounts of random data to trick the system) to unit tests (checking individual parts of the application), it’s crucial to test a project’s resistance to various attack scenarios.
- Manual code review: Human intuition and expertise still play a substantial role in identifying and solving issues within a smart contract. This step backs up automated testing and can spot discrepancies even the most advanced automated tests might miss.
- Use of secure dependencies: It is crucial to verify the security of third-party smart contracts before incorporating them into a project. Trusted libraries should always be preferred over creating code from scratch.
- Writing clear & simple code: The simpler, clearer, and more transparent the code, the better. Complex code not only fosters potential security risks but also makes auditing more difficult.
- Keeping contracts upgradable: Ensuring that smart contracts are upgradable can be one effective way to resolve issues in the aftermath of a vulnerability disclosure.
Equip your smart contracts with these strategies to effectively protect against known vulnerabilities and be prepared to tackle unforeseen security challenges.
The audit process in a nutshell
Now that we understand the importance of a smart contract audit and its benefits, let’s dive deeper into what the audit process entails. It’s a complex but necessary task that involves several key stages.
Step 1. Collect documentation
For the audit to begin, the project undergoing the audit must instigate a code freeze, effectively locking the existing state of the project’s code. They then provide the auditors with all relevant technical documentation—this can range from the codebase to specific technical specifications, white papers, and architectural diagrams. This documentation provides critical context and guides the auditors in understanding the project’s goals, scope, and implementations.
Step 2. Automated testing
Auditors employ a formal verification engine, also known as an automated testing mechanism. This engine carries out an extensive check of every conceivable state of the smart contract and alerts the auditors to any issues potentially compromising the contract’s functionality or security. Auditors also conduct additional tests on individual functions and perform penetration testing, a simulated cyber attack on the smart contract, to study the contract’s response and locate any security vulnerabilities.
Step 3. Manual review
Manual code reviews follow automated testing. Here, an experienced team of security experts meticulously examines each line of the smart contract to identify anomalies and vulnerabilities. While automated tests are efficient at identifying bugs in the code, human engineers are better equipped to uncover issues like discrepancies in contract logic or architecture and opportunities for gas optimization—problems often overlooked by automated tools.
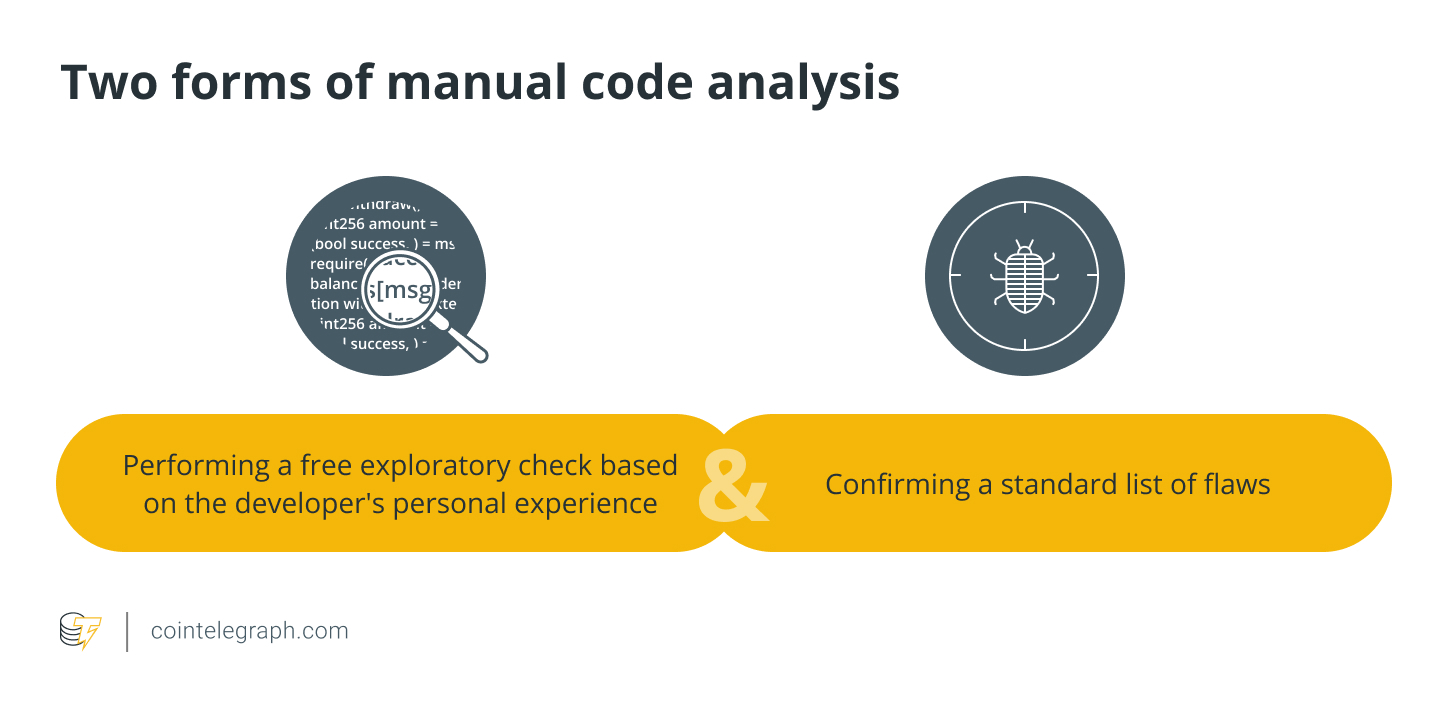
Step 4. Classification of contract errors
Each vulnerability is then categorized based on its severity:
- Critical: These issues impact the protocol’s safe functioning.
- Major: These are typically centralization and logical errors that could lead to loss of user funds or loss of control over the protocol.
- Medium: These issues affect the performance or reliability of the platform.
- Minor: These involve inefficient code that, while not immediately dangerous, is best avoided.
- Informational: These relate to style or best practices within the industry.
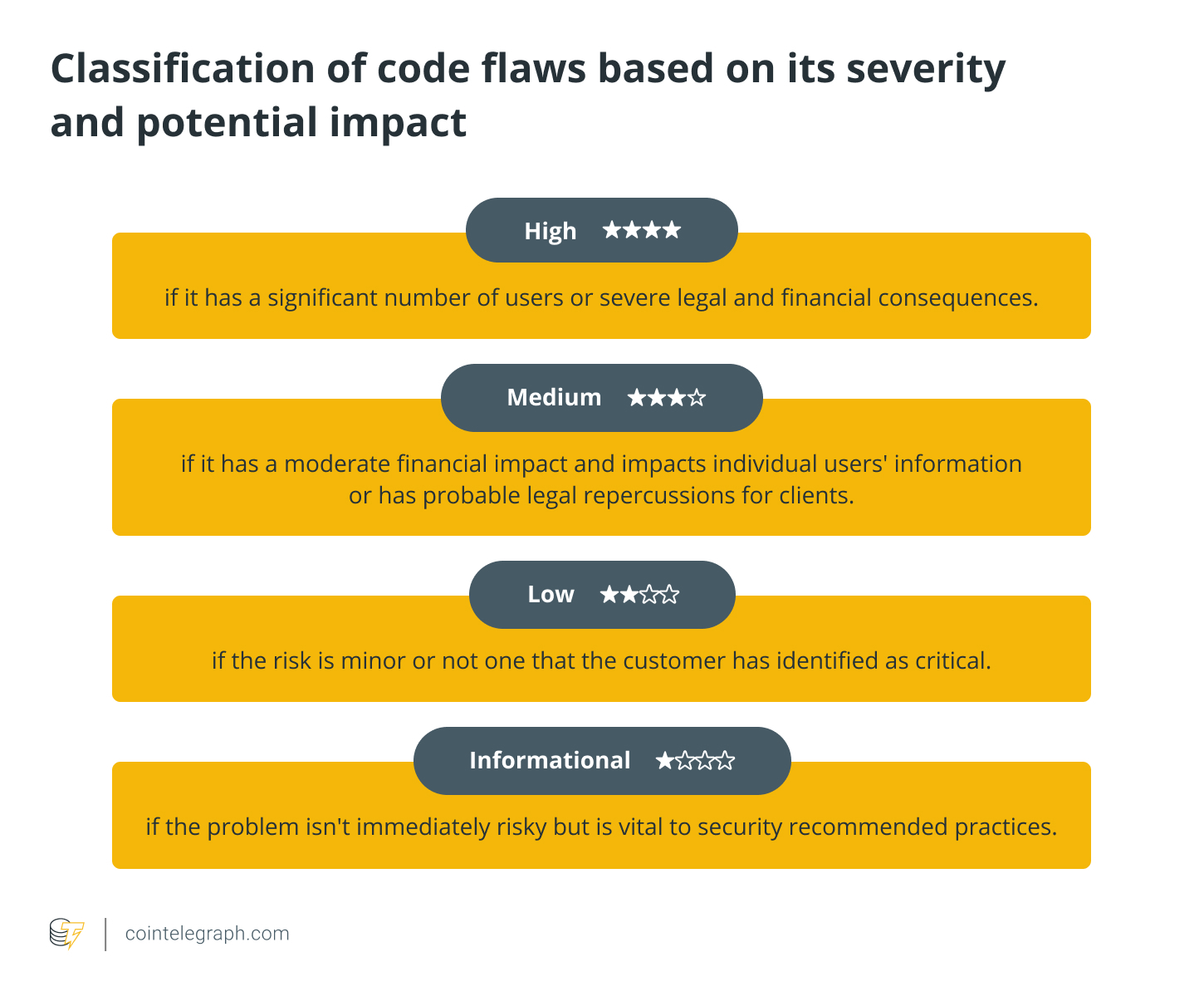
Step 5. Initial report
Following this, auditors draft an initial report summarizing the discovered flaws and suggest potential solutions to these issues. Some smart contract service providers have dedicated experts who can assist in fixing the identified bugs. By addressing all deficiencies, projects can deploy smart contracts, secure in the knowledge they are optimized for potential threats.
Step 6. Publish final audit report
Finally, the auditor generates a comprehensive report detailing all discoveries. This report marks all identified issues as either resolved or unresolved. The project team receives this report and usually, make it public, enabling all stakeholders (users, investors, partners) to have full transparency into the security of the protocol.
The audit, though intricate and time-consuming, remains an important hurdle a project must clear to ensure it is secure and ready for actual deployment. Find out more about the security policies we have implemented on the Chainstack platform for your convenience here.
Further reading
- SOC 2 Type 1 and our commitment to secure Web3 infrastructure: Build securely with Chainstack’s SOC 2 Type 1 certified infrastructure.
- Unmasking DApp endpoint security: Explore our research findings on DApp endpoint security across 8,000+ projects, revealing crucial vulnerabilities across Web3.
- CertiK on Chainstack: See how CertiK cut Ethereum archive costs by 70%+ with Chainstack for its radical take on Web3 security, from audits to real-time monitoring.
- Hypernative on Chainstack: Discover how Hypernative reinforces Web3 security with resilient Chainstack infrastructure, optimizing asset protection and efficiency.
- FailSafe on Chainstack: Discover how Chainstack infrastructure revolutionizes FailSafe’s Web3 security to reduce latency, boost transaction volumes, and user safety.
- Wallet security best practices: Learn the basics of protecting your digital assets securely.
Bringing it all together
The world of smart contracts is booming, bringing exciting opportunities for many industries. However, with new technologies come new challenges and potential vulnerabilities. To ensure the success and security of these revolutionary protocols, smart contract security audits have become an imperative.
These audits, encompassing both automated and manual checks, bring a high level of scrutiny to catch and classify potential vulnerabilities and weak points. From reentrancy issues to intrinsic issues like integer overflow, audits help protect against common security threats. They bring a magnifying glass to a contract’s code, clearing the path to a secure and efficient deployment.
Vigilance in the face of potential risks and dedicated attention to best practices can help ensure the integrity of a project’s blockchain endeavors. Regular audits, secure dependencies, and upgradability are some solutions that, when incorporated within a development strategy, help fortify smart contracts and safeguard them against threats and exploitation.
Smart contract audits are more than just a security measure. They instill confidence—confidence among the development team that they are creating a more secure protocol and confidence among users that their funds are protected. In the fast-paced, ever-evolving world of blockchain, this sense of trust is priceless.
Power-boost your project on Chainstack
- Discover how you can save thousands in infra costs every month with our unbeatable pricing on the most complete Web3 development platform.
- Input your workload and see how affordable Chainstack is compared to other RPC providers.
- Connect to Ethereum, Solana, BNB Smart Chain, Polygon, Arbitrum, Base, Optimism, Avalanche, TON, Ronin, Plasma, Hyperliquid, Scroll, Aptos, Fantom, Cronos, Gnosis Chain, Klaytn, Moonbeam, Celo, Aurora, Oasis Sapphire, Polygon zkEVM, and Bitcoin mainnet or testnets through an interface designed to help you get the job done.
- Fast access to blockchain archive data and gRPC streaming on Solana.
- To learn more about Chainstack, visit our Developer Portal or join our Telegram group.
- Are you in need of testnet tokens? Request some from our faucets. Sepolia faucet, Hoodi faucet, BNB faucet, zkSync faucet, Scroll faucet, Hyperliquid faucet.
Have you already explored what you can achieve with Chainstack? Get started for free today.
 Ethereum
Ethereum Solana
Solana Hyperliquid
Hyperliquid Base
Base BNB Smart Chain
BNB Smart Chain Monad
Monad Aptos
Aptos TRON
TRON Ronin
Ronin zkSync Era
zkSync Era Sonic
Sonic Polygon
Polygon Unichain
Unichain Gnosis Chain
Gnosis Chain Sui
Sui Avalanche Subnets
Avalanche Subnets Polygon CDK
Polygon CDK Starknet Appchains
Starknet Appchains zkSync Hyperchains
zkSync Hyperchains