Unmasking DApp endpoint security: The Chainstack research results

The rapid growth of decentralized applications (DApps) has unlocked new possibilities for a decentralized digital future. However, the security of these applications is just as much of a crucial factor in determining their success as their overall adoption is.
That is why, we set out to explore the current state of the Web3 landscape in our recent study, specifically aiming at unmasking DApp endpoint security. We conducted the research over a data set of nearly 8 000 individual projects, uncovering a significant share of alarming results and major reasons for concern across multiple verticals and protocols.
In this blog post, we will delve into the key findings of our study, shedding light on project activity, DApp integrity, common cloud service providers, RPC endpoint exposure, and the node provider it originates from, as well as endpoint sharing and whitelisting practices. And by raising awareness of the issues present in each category, we strive to foster a more secure and reliable decentralized landscape, ultimately building trust and ensuring the continued growth of the industry.
You can find the full research paper available for download freely at the bottom of this post here.
The Importance of endpoint security in decentralized applications
As the DApp landscape grew, with a 50% increase in unique active wallet data from 2021 to 2022, security concerns, especially endpoint security, have escalated. Generally speaking, endpoints are vulnerable due to the variety of platforms and media they originate from, the vast number of devices using them, and the plethora of ways user interactions take place.
Studies have identified several attack vectors aimed at endpoints in the Web3 context, including vulnerabilities like Sybil attacks, private key leaks, mining malware, and cryptojacking. To address these concerns, experts suggest moving authentication, authorization, and policy enforcement closer to network edges and endpoints.

As the number of users and devices interacting with blockchain networks and decentralized applications increases, organizations must invest in robust, well-integrated security strategies to protect their assets and data. This involves focusing on endpoint security measures, staying informed about the latest trends and threats, and fostering a culture of security awareness and responsibility among employees.
Collaboration between industry players, academia, and regulatory authorities is crucial for tackling endpoint security challenges in the DApp landscape. By sharing knowledge, resources, and best practices, stakeholders can work together to develop innovative solutions and create a more secure and resilient decentralized ecosystem.
Investigating DApp endpoint security: Methodology and research questions
In our study, we explored endpoint security vulnerabilities in decentralized applications by examining a diverse sample group using a custom-built data collection tool. Our research aimed to fill knowledge gaps by gathering concrete technical parameters and employing inductive analysis techniques to identify patterns to refine our theoretical framework.
Our research questions targeted critical aspects of DApp endpoint security, including concerns and vulnerabilities across verticals and protocols, variations in endpoint exposure among different sectors, the prevalence of certain node and cloud service providers, as well as the presence of whitelisting practices to provide adequate recommendations for further security improvements.
We addressed five main research questions:
- What is the current state of the DApp ecosystem, in terms of project activity and the overall technical integrity of the services being offered?
- What are the critical concerns and vulnerabilities associated with DApp endpoint security, across various verticals and protocols?
- How does the level of endpoint exposure vary among different verticals and protocols and which of them are most prone to poor security practices?
- Which are the most commonly used node and cloud service providers for DApp projects and the ones typically affected by poor endpoint security?
- How prevalent is the practice of whitelisting among fully exposed DApp endpoints and how does it differ across various protocols and verticals?
We selected 8 157 DApps as data points for our research, representing various use case verticals, including Collectibles, DeFi, Gambling, Games, Marketplaces, Social, High-Risk, and Other. It is important to note this number amounts to 7 343 if you count multi-chain projects as a single entity.
Our custom-built web scraper tool collected relevant data from these DApps by doing DNS as well as Autonomous System (AS) lookups while examining their network activity for Fetch/XHR requests to Web3 RPC endpoints. We then assessed the presence of additional security measures for these RPC endpoints by performing simple cURL requests to determine whether they had whitelisting enabled.
The findings of this study are meant to serve as a foundation for further research while offering valuable insights for Web3 organizations interested in enhancing DApp security as well as individuals evaluating the safety of their assets. The data collection instrument itself also presented potential ideas for further academic investigation of the subject matter and related topics.
Key findings from the study
In this section, we will delve into the essential insights and notable trends brought to light by the comprehensive research we conducted on the decentralized application landscape. By sharing these findings, we strive to provide a better understanding to the general public of the current state of the DApps ecosystem, along with the implications of poor security on the industry’s future as a whole.
Project activity: Mapping out the current DApp landscape
Of the 8 157 DApps we analyzed, just over half (54%), or 4 424 to be exact, could be deemed active, which left a gaping hole of 3 733 inactive ones from the 46% that remained. This served to emphasise the importance of understanding the reasons for project inactivity across verticals and protocols.
When we omitted DApps with multi-chain deployments, DeFi, High-Risk, and Games emerged as the leading verticals for the 7 343 unique projects. Consequently, they accounted for segments of 28%, 24%, and 17%, respectively, while the remaining verticals made up 31% of the total DApp tally.
High-Risk and Gambling projects showed higher rates of inactive DApps, reflecting a possible lack of trust in these use cases. In contrast, Collectibles and Marketplaces, though smaller in numbers, had nearly 76% DApp activity rates, suggesting higher trust levels and long-term user engagement.

Binance Smart Chain (BNB) and Ethereum were the most widely used protocols for DApps, with 43% and 37% shares, respectively. Both had an inactive DApp rate of approximately 49%. DeFi, the most popular vertical overall, boasted a high rate of active DApps on Ethereum and Avalanche with 77%.
BNB, on the other hand, featured a higher percentage of DApps in the High-Risk sector, possibly due to the lower cost barriers involved in developing a project on the protocol, while Ethereum hosted a smaller portion of High-Risk DApps but experienced a higher inactivity rate for them overall.

DApp integrity: Separating legitimate and disreputable projects
Despite there being a real potential for fraudulent activity, our findings indicated that the actual prevalence of such activities was relatively minimal. Out of the 8,157 DApps analyzed, a mere 1.6% were classified as disreputable. When considering their proportion among active DApps instead of the total count, this figure rose only slightly, to just under 3%. This modest number indicated that disreputable projects were the exception rather than the norm, which is sure to put many at ease.

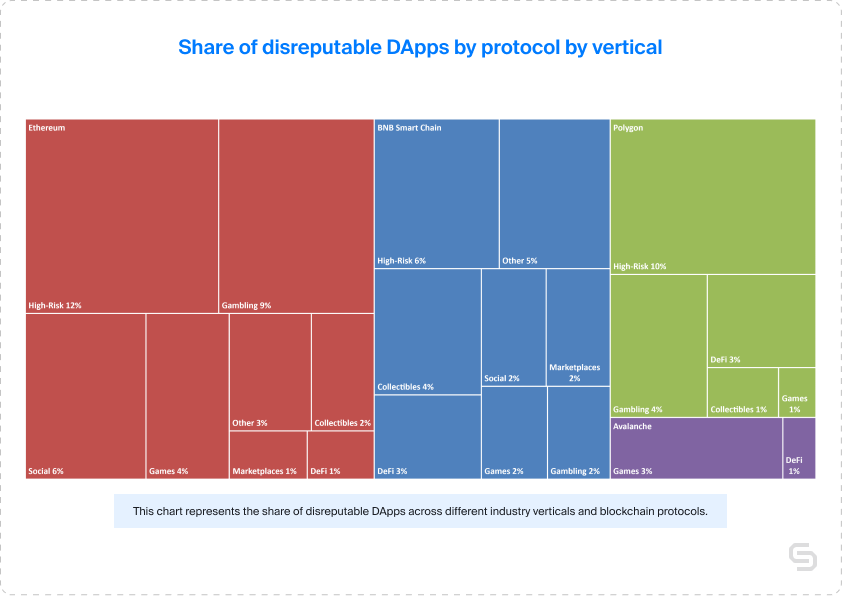
A look into disreputable DApps across various verticals showed that DeFi was the most common one, with 2.5% of its active projects classified as such. High-Risk and Gambling verticals had the highest rates at 7% and 6.5%, respectively. In contrast, marketplace projects exhibited the lowest rate of 1.6%, while social projects ranked third highest at 3.7%. Other, Gaming and Collectibles displayed relatively low rates of 3.1%, 2.7%, and 2.2% in the same order.

When evaluating disreputable DApps by protocol, BNB had the highest number and percentage (61 DApps for 3.5%), followed by Ethereum with 3.1% from 49 DApps. Polygon had 20 such projects for 2.5%, while Avalanche had only 0.7% from just 2. A deeper analysis of the data by both protocol and vertical revealed that High-Risk projects had the highest rates across BNB, Ethereum, and Polygon.
Cloud service provision: An overview of common Web3 hosting options
Cloudflare led the Web3 cloud service provider market with a 35% share, followed by Amazon Web Services (AWS) at 19%, and Vercel and Google Cloud Platform with approximately 10% each. Other providers, including Fastly, Namecheap, DigitalOcean, Hostinger, OVH, and Bodis, collectively accounted for 12% of active projects.
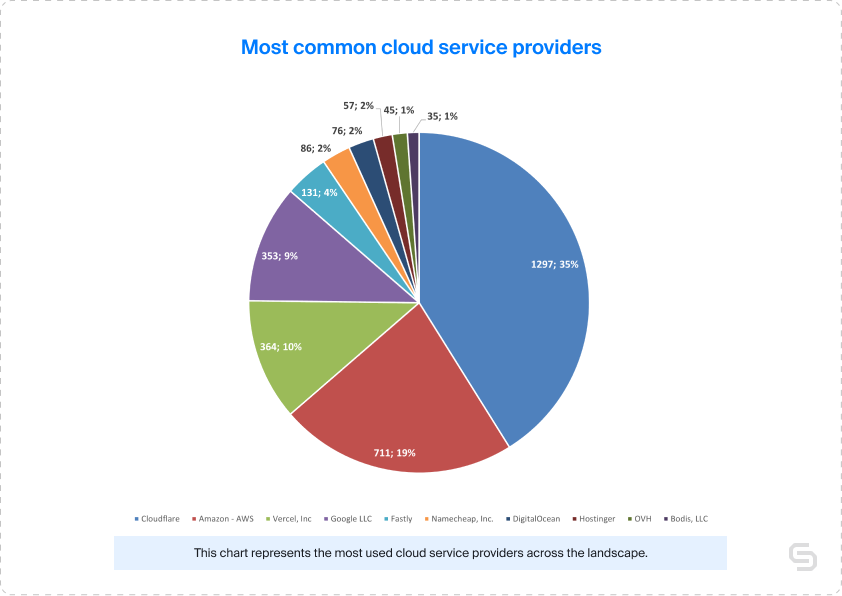
When examining cloud service provider preferences across various verticals and protocols, Cloudflare consistently ranked as the most popular choice. Regardless of the sector, the top four providers remained relatively consistent, with Cloudflare at the top, while AWS, Google, and Vercel contested over the remaining slots in the bracket.
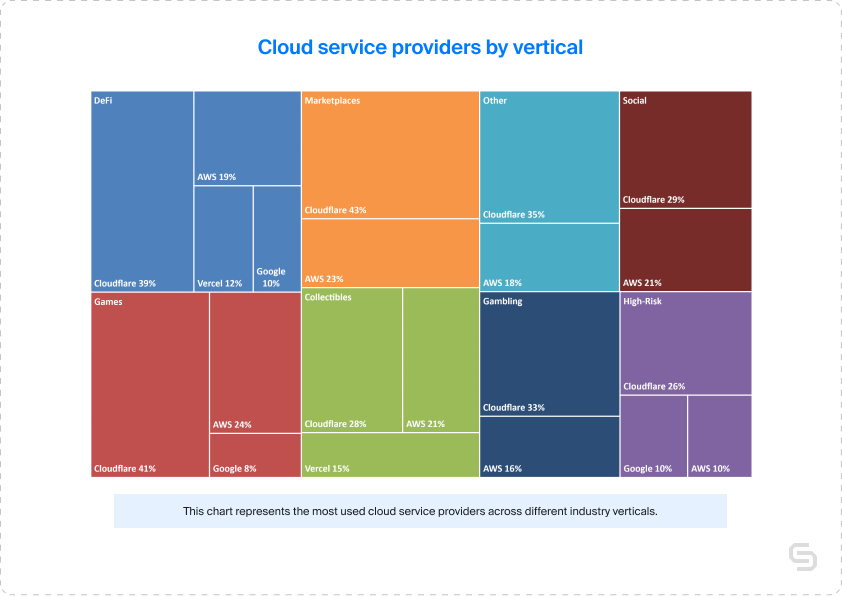
In conclusion, while Cloudflare remained the market leader in the Web3 cloud service provider landscape, a closer examination revealed a more nuanced story. Providers such as Vercel, Amazon, and Google did seem to be gaining traction in specific verticals and protocols, with Vercel emerging as a popular choice for niche use cases in Web3.
Overall RPC endpoint exposure: evaluating partial and full exposure
Our study of 3 731 individual active DApps discovered that 1,385 (37%) have exposed RPC endpoints on the front-end. This number is quite significant, considering such vulnerabilities pose a significant risk for user data and interactions, as visible RPC endpoints can lead to loss of funds or unauthorized malicious actions. Despite many projects adhering to endpoint security best practices, the large share of exposed endpoints highlights the need for fundamental improvements in security across Web3.
DeFi projects accounted for the highest segment of DApps with exposed endpoints with their 62.8%, followed by Ethereum with half this number, or 20.9% to be exact. When it came to BNB, it exhibited the largest share of 38.4%, while Polygon and Avalanche claimed 34% and 37.6%, respectively. This data underscores the urgency of security improvements for projects built on BNB, although other protocols need to address endpoint security too, particularly those with higher shares of exposure.
Avalanche Collectibles, Polygon DeFi, and BNB Smart Chain DeFi had the most significant exposure shares of 64%, 52%, and 51%, respectively. This highlighted the necessity for swift resolution and increased user vigilance in these categories. Although certain sectors, such as Ethereum Gambling, High-Risk, Games, and Other, exhibited lower exposure shares, the need for better endpoint security is still there and must be a priority for all developers contributing to the DApp ecosystem.

Fully exposed RPC endpoints: Verticals and protocols with the highest vulnerabilities
In our analysis, it was crucial to distinguish between DApps with partially exposed RPC endpoints and those with full exposure. This is so, as full endpoints allow unrestricted external access to their API, enabling anyone to execute commands unobstructed and exposing them just makes it all too easy.
The good news was that out of 3 731 individual active projects, only 391 or roughly 10% had fully exposed endpoints. However, this context became more alarming when comparing partially exposed DApps with those with full exposure. Of 1 385 DApps with exposed RPC endpoints, 994 (72%) were not fully exposed, leaving a concerning 28% segment that is entirely open and publicly interactable.
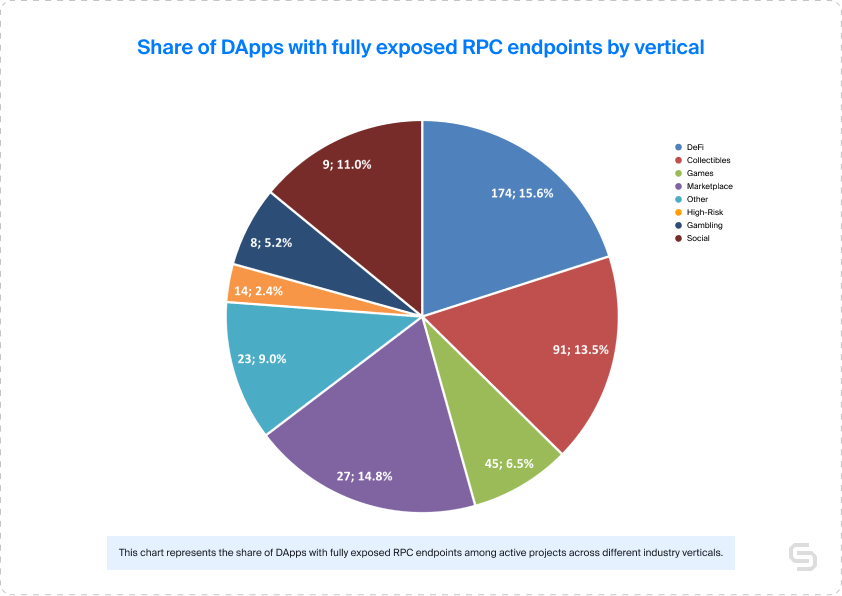
Examining the data by verticals revealed that DeFi, Marketplaces, and Collectibles had the highest shares of projects with fully exposed endpoints, which is particularly concerning as these verticals carry the largest liabilities. In DeFi, these were 15.6%, while Marketplaces and Collectibles had shares of 14.8% and 13.5%, respectively.
When analyzing the data by protocol, Ethereum stood out with the highest quantity and share of fully exposed RPC endpoints. From the tally of 276 DApps with fully exposed endpoints, Ethereum had a 17.5% share, nearly twice as much as Polygon’s 9.6%. When considering the share of fully exposed endpoints from active projects, Ethereum and Polygon were equally matched at 3% each.
Investigating the data through a combined lens of protocol and vertical, Ethereum DeFi emerged as the category needing the most improvement, with a 31% share of DApps with fully exposed endpoints. Other Ethereum verticals such as Marketplaces, Social, and Collectibles exhibited lower shares at 19%, 16%, and 15%, respectively. Without Ethereum DeFi in the dataset, the results across all protocols would have been more balanced, fluctuating between 10% and 15%.
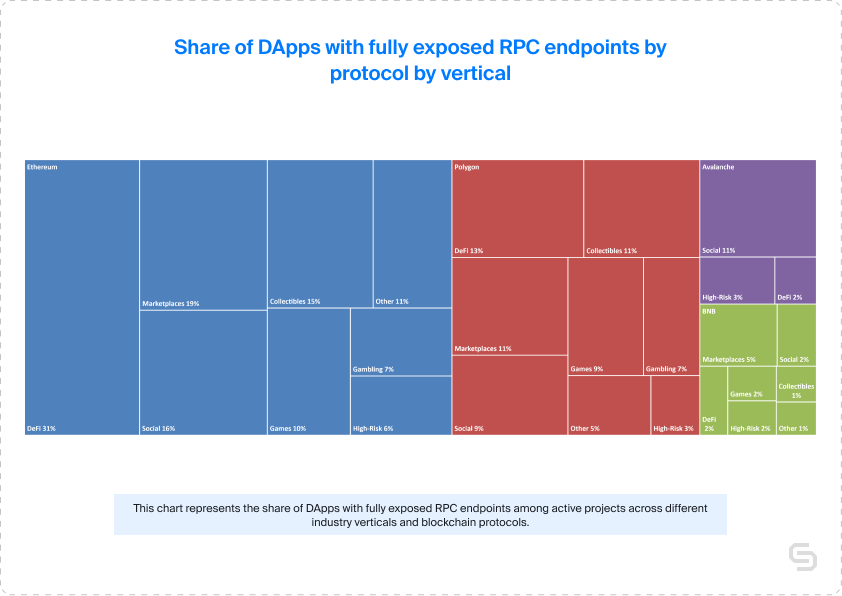
Node service provider prevalence among DApps with RPC endpoint exposure
Keeping in mind the fact that some DApps made use of more than one provider, we didn’t explore this particular subject on an individual project basis. Instead, we took into consideration the entirety of the data set, without counting multiple exposed endpoints as a single one.
Among the entire tally of 1 540 exposed RPC endpoints, a significant share of 51.6% were public endpoints, which was unsurprising, considering their cost-free nature and general availability. As a consequence, there was possibly less of an incentive to secure them, leading to higher exposure.
Setting aside the public endpoints for a moment, we found that Ankr and Infura took the second and third spots, with 15.7% and 14.7% of the exposed endpoints, respectively. Alchemy came in fourth place, representing 8.9% of the total.

The remaining providers, including Quicknode, Chainstack, Nodereal, Cloudflare, Pocket Network, and Moralis, did not offer statistically significant results for adequate analysis on their own. When aggregated, they approached the figures held by the fourth-place contender, Alchemy.
When we took a closer look at the data by verticals, we could see that High-Risk, Games, and Other had the largest share of exposed public endpoints at 65%, 52%, and 51% respectively. On the other hand, Infura and Ankr dominated Collectibles and Gambling with 31% and 26%, for non-public ones.
The results varied when examining the data by protocol, as both BNB and Avalanche predominantly featured exposed Public endpoints at 88% and 86%, respectively. Ethereum and Polygon, however, showed a more balanced distribution with Infura and Ankr holding the largest segments at 52% each.
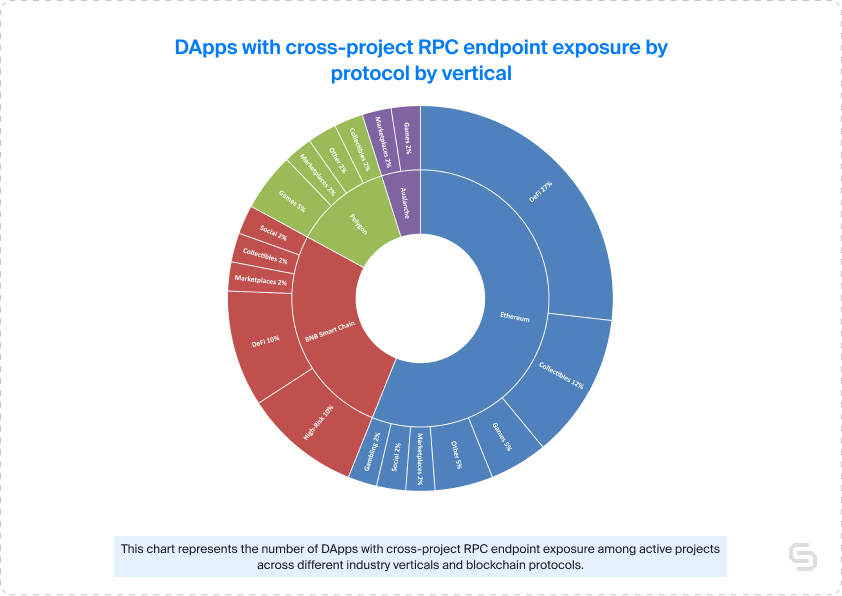
Cross-project exposure: A pressing yet less prevalent concern
When examining the data set of 41 DApps with shared exposed RPC endpoints, we found that High-Risk, Social, and Marketplaces verticals had the highest prevalence, claiming 20%, 20% again, and 14% shares respectively. In absolute terms, this translated to 4, 2, and 2 DApps in each category. But due to these low absolute values, the need for further investigation here was especially pronounced.
Analyzing the data by protocol revealed that Avalanche and BNB Smart Chain exhibited the worst results in terms of cross-project RPC exposure, with 40% and 34% of their fully exposed endpoints respectively. However, due to the small sample sizes, especially for Avalanche, these findings could not be deemed statistically conclusive. Ethereum and Polygon protocols, on the other hand, had a lower share of fully exposed endpoints with cross-project exposure at 8% and 6% respectively.
When examining the data by protocol and vertical, Ethereum emerged as the dominant protocol for cross-project RPC exposure, accounting for 56.1% of all shared fully exposed RPC endpoints. Within Ethereum, DeFi was the vertical with the highest share with 27%, followed by Collectibles at 12%. In turn, BNB Smart Chain had two on par with 10% segments – the High-Risk and DeFi verticals.
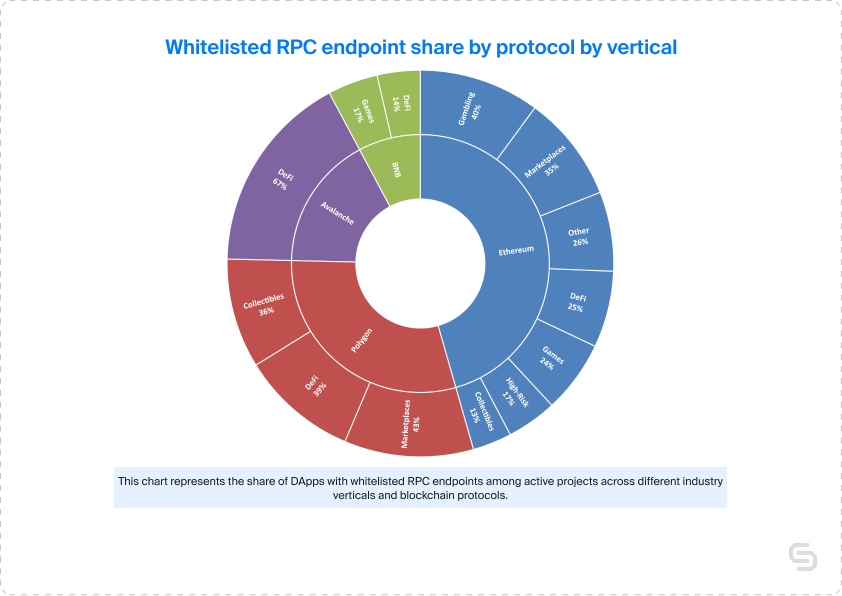
Current state of whitelisting in the DApp ecosystem
In an effort to understand the presence of the whitelisting security practice in the DApp ecosystem, we analyzed a sample of 422 fully exposed endpoints. Not even a quarter of these, or 92 to be exact were found to have implemented such policies, indicating that an incredibly large portion remained unprotected against potential malicious activities.
When examining the data by vertical, we found that Marketplaces, DeFi, Gambling, and Other had the highest share of whitelisted fully exposed endpoints, with 32%, 28%, 25%, and 22% respectively. However, not all of these verticals had statistically significant sample sizes, with Gambling and Other having the least number of endpoints. While Marketplaces, Games, and High-Risk verticals had more endpoints in their samples, their whitelisted segments were just 15% and 6% respectively.
When analyzing the data by protocol, Ethereum and Polygon had the largest and most statistically significant sample sizes, with 66 and 21 endpoints respectively. Both protocols had roughly a quarter of their fully exposed endpoints whitelisted (22% for Ethereum and 27% for Polygon). Conversely, BNB had a lower such share of just 9%, and given its larger overall sample size, BNB could be labeled as the least protected protocol in terms of whitelisting presence in fully exposed RPC endpoints.
Conclusions and recommendations for further improvement
Our study revealed several security concerns for the DApp ecosystem. A notable percentage of active projects had exposed RPC endpoints, whether partially or fully, with Ethereum, particularly its DeFi vertical, being the most vulnerable. That is why, we recommend that developers prioritize securing their DApps’ RPC endpoints, especially in the DeFi, Marketplaces, and Collectibles sectors. Overall, users should exercise caution when interacting with projects that have fully exposed RPC endpoints.
Additionally, our analysis found that Public endpoints made up a significant share of exposed RPC endpoints, with High-Risk, Games, and Other verticals having the largest share of exposed public endpoints. To improve security, we encourage raising awareness on public endpoint security, calling for node service providers to enhance their security measures, and conducting further research to help shed even more light on specific vulnerabilities within each vertical and protocol.
Lastly, our investigation of endpoint access exposure revealed that only a small percentage of fully exposed DApp endpoints were whitelisted, indicating a significant need to implement better security practices. We encourage DApp developers to make use of whitelisting and avoid front-end visibility of their endpoints, especially in verticals with lower rates of adoption. Focus should also be given to projects deployed on protocols that tend to have less protected endpoints, such is the case for BNB.
Building a secure and reliable decentralized infrastructure
That being said, our comprehensive study of DApp endpoint security did uncover critical concerns and vulnerabilities across various verticals and protocols. With 10% of active DApps having fully exposed RPC endpoints, the potential risks to users and developers are significant, particularly in the DeFi, Marketplaces, and Collectibles sectors. Ethereum, as the protocol with the highest number of projects with fully exposed RPC endpoints, requires urgent attention, especially in its DeFi vertical.
Cross-project exposure and the lack of whitelisting implementation in the DApp ecosystem further compounded the security challenges. High-Risk, Social, and Marketplaces verticals stood out as the ones with the highest shared endpoint exposure, while just about 22% of fully exposed ones overall employed whitelisting, a vital security practice. All of this highlighted the need for increased efforts in promoting and implementing endpoint security best practices further across the entire landscape.
To ensure a more secure and reliable DApp experience, we propose preventive actions, including prioritizing the securing of RPC endpoints in critical sectors, enhancing and promoting existing node provider policies, as well as encouraging the adoption of whitelisting among DApp developers. By following these recommendations, we can foster trust and facilitate the ongoing growth and success of the decentralized applications landscape, benefiting users, developers, and service providers alike.
Get the Endpoint secrets exposed study PDF
Download the full Endpoint secrets exposed: A tale of 8000 DApps research paper for free:
Power-boost your project on Chainstack
- Discover how you can save thousands in infra costs every month with our unbeatable pricing on the most complete Web3 development platform.
- Input your workload and see how affordable Chainstack is compared to other RPC providers.
- Connect to Ethereum, Solana, BNB Smart Chain, Polygon, Arbitrum, Base, Optimism, Avalanche, TON, Ronin, zkSync Era, Starknet, Scroll, Aptos, Fantom, Cronos, Gnosis Chain, Klaytn, Moonbeam, Celo, Aurora, Oasis Sapphire, Polygon zkEVM, Bitcoin and Harmony mainnet or testnets through an interface designed to help you get the job done.
- To learn more about Chainstack, visit our Developer Portal or join our Discord server and Telegram group.
- Are you in need of testnet tokens? Request some from our faucets. Multi-chain faucet, Sepolia faucet, Holesky faucet, BNB faucet, zkSync faucet, Scroll faucet.
Have you already explored what you can achieve with Chainstack? Get started for free today.
 Ethereum
Ethereum Solana
Solana TON
TON Base
Base BNB Smart Chain
BNB Smart Chain Sui
Sui Unichain
Unichain Aptos
Aptos TRON
TRON Ronin
Ronin zkSync Era
zkSync Era Sonic
Sonic Polygon
Polygon Gnosis Chain
Gnosis Chain Scroll
Scroll Avalanche Subnets
Avalanche Subnets Polygon CDK
Polygon CDK Starknet Appchains
Starknet Appchains zkSync Hyperchains
zkSync Hyperchains