Stealth Addresses: Decrypting blockchain transaction privacy

Living in the world of Web3, privacy remains an enigma. On one hand, we applaud blockchain technology for its transparency, decentralization, and immutable transactions; on the other, we despair at its inability to offer complete anonymity.
This friction between the need for privacy and the openness of the blockchain is striking. The answer? Stealth Addresses.
Born out of a need for better privacy in transactions, Stealth Addresses are an innovative approach, ensuring confidentiality while receiving funds, and hence are increasingly finding significance in the crypto universe. Let’s explore the details.
What are Stealth Addresses?
Stealth Addresses are a unique solution to the pressing issue of privacy in public blockchain records. Contrary to what we see in ordinary transactions where the recipient address is visible, Stealth Addresses aim to make these transactions as anonymous as possible.
The concept of Stealth Addresses came into existence back in 2014, proposed by Peter Todd. These addresses use the elliptic-curve Diffie-Hellman protocol, which is essentially about establishing shared secrets over insecure channels, to provide privacy during transactions. When transacting parties use Stealth Addresses, it ensures that they continue to operate privately, while the recipient can check their transactions using a special “spending key.”
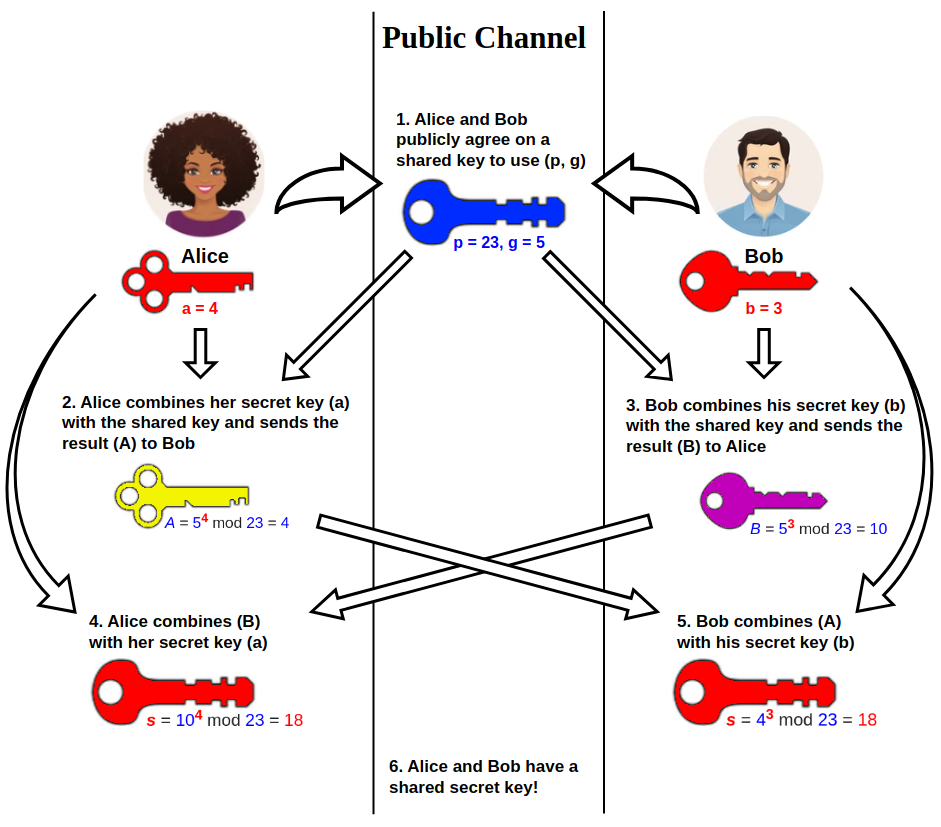
Each Stealth Address is unique, used only once, and remarkably, even multiple transactions coming in from the same recipient don’t change this fact. The best part? This upgrade from ordinary wallet addresses to Stealth Addresses does not necessitate heavy adjustments from the users—instead, the entire process remains largely similar to how transactions were made using pre-existing tech.
Why are Stealth Addresses important?
It’s high time we understood and clarified a common misconception about cryptocurrencies—they are not intrinsically anonymous! Although it might appear as though having a wallet provides you with a digital mask, that isn’t entirely true. A public blockchain network, in essence, is a shared database—minutely inspect it, and you’ll find each party’s addresses and transaction amounts out in the open for everyone to see.
The issue arises when an address owner’s identity is discovered. Suddenly, the so-called “anonymous” transaction isn’t anonymous anymore. Hence, it becomes abundantly clear why Stealth Addresses are such a crucial addition to Web3, enabling users to maintain their privacy while carrying out transactions.
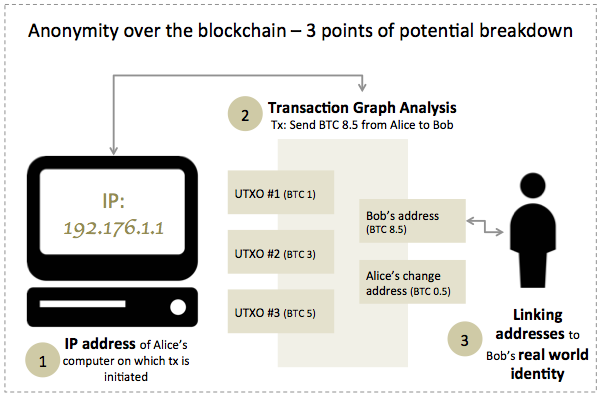
Issues with public blockchain records
Public blockchain records are designed to be transparent and immutable, two features that contribute significantly to the trust users place in the blockchain. However, these strengths can also become weaknesses when it comes to privacy.
Public blockchain records display the wallet addresses involved in a transaction and the amount transferred. This information is openly accessible to anyone via a blockchain explorer.
While this transparency allows for auditing and accountability, it also means that once an individual’s wallet address becomes linked to their real-world identity, their entire transaction history can potentially be traced and analyzed by any third-party observer. Consequently, this lack of privacy can expose users to numerous risks, including personal security threats or analysis of financial behavior.
Reasons for generating one-time Stealth Addresses
Blockchain technology might promise pseudonymity, not anonymity. When your name or any other identifiable data becomes associated with your public wallet address, your security is compromised.
Situations where you must share your wallet address online expose you to potential threats. Moreover, if you transfer crypto from platforms where you have undergone KYC verification, that address becomes a point of possible privacy failure.
The possibility of tracing transactions back to wallets might seem trivial at first but it can have severe implications. Stealth Addresses have been proposed and used as a potential solution to this issue.
They allow you to keep your real wallet address hidden, which can act as a deterrent for would-be trackers. Stealth Addresses essentially work as your digital PO Box or a VPN network masking your computer’s IP address—they keep your personal information obscured, making any incoming transactions untraceable.
In Web3, where transactions are digitized and easy to trace, Stealth Addresses are a step towards maintaining the balance between security, transparency, and the much-needed privacy of users.
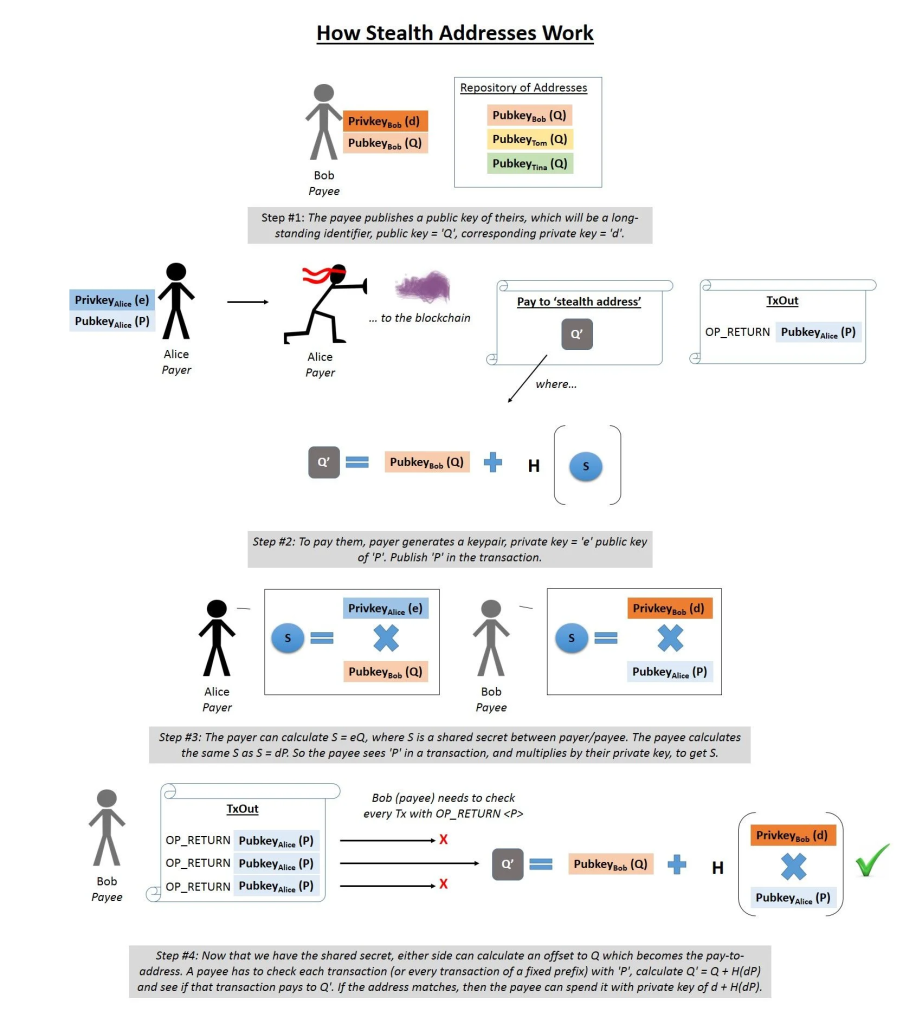
How Stealth Addresses work
In traditional blockchain transactions, a sender requires the recipient’s public wallet address to transfer funds. However, this leads to a significant privacy issue: if a wallet address is connected to a real-world identity, all transactions involving it become traceable. Stealth Addresses were developed to address this concern.

Stealth Addresses increase security and anonymity by creating a unique, one-time address for each transaction. Consequently, even if a recipient gets multiple transactions, each is linked to a different address, enhancing privacy.
The spending key in Stealth Addresses
Firstly, “Bob,” the recipient, creates a “spending key.” This key is a secret private key that Bob will use to spend the funds he receives. It plays a pivotal role in ensuring that only Bob can access and use the funds sent to him.
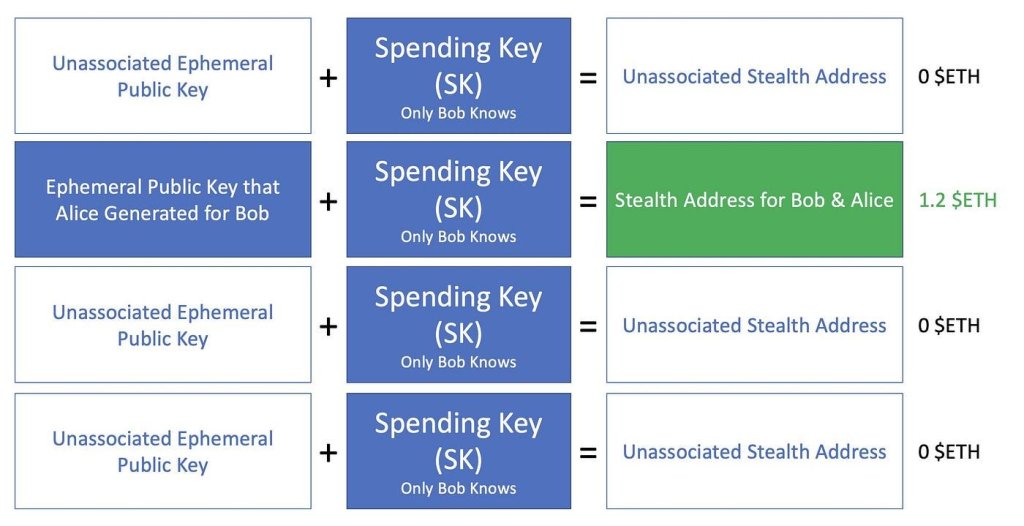
The meta-address of Stealth Address transactions
Bob uses his spending key to generate a stealth “meta-address.” This meta-address is then shared with “Alice,” the sender. Alice will use this meta-address in the next step to craft an ephemeral key.
The ephemeral key for Stealth Addresses
Creating a Stealth Address involves the sender (“Alice”) generating a one-time or ephemeral key. This key is a single-use random number that Alice uses, along with Bob’s public key, to create the Stealth Address as per the guidelines defined within the Elliptic-curve Diffie-Hellman protocol. Upon completing the transaction, Alice includes the ephemeral key within the transaction data on the blockchain.
Once the Stealth Address has been generated, Alice can proceed to send her assets to that address. Alice also releases an additional piece of cryptographic data on-chain: the “ephemeral public key.”
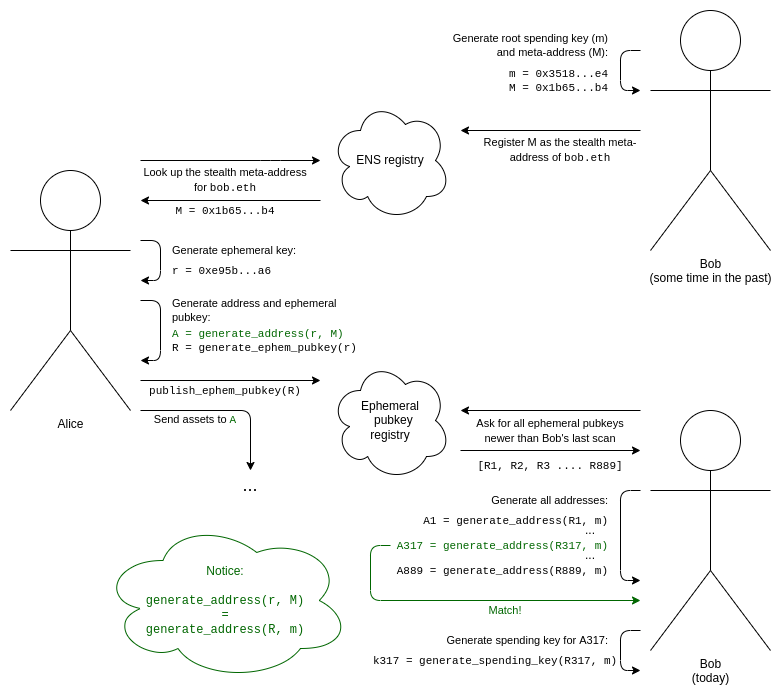
Though Stealth Addresses add an additional layer of privacy, the transactions between Alice and Bob remain transparent and trackable on the blockchain. Yet, the true identity of Bob’s actual address is concealed, maintaining an anonymous transaction between Alice and Bob. Alice’s transfer to the Stealth Address can be observed by others on the network, but it is impossible for them to connect this transaction back to Bob.
This method ensures that each transaction to the same recipient appears unlinked, enhancing privacy without compromising the blockchain’s inherent transparency. Through this intricate process, Stealth Addresses create a balance between privacy and transparency, allowing for secure, anonymous transactions on a public ledger.
Advantages and challenges of Stealth Addresses
Stealth Addresses bring to the table a wealth of advantages over existing privacy solutions in the blockchain world. First and foremost, they provide transactional privacy on a public blockchain. Even when multiple transfers are executed from the same sender, Stealth Addresses ensure every transaction appears to be to a different and unlinked recipient.
Owing to their distinctive creation procedure, Stealth Addresses allow for novel financial privacy protections. They offer a solution to the inherent risk of address reuse, making tracking more difficult.
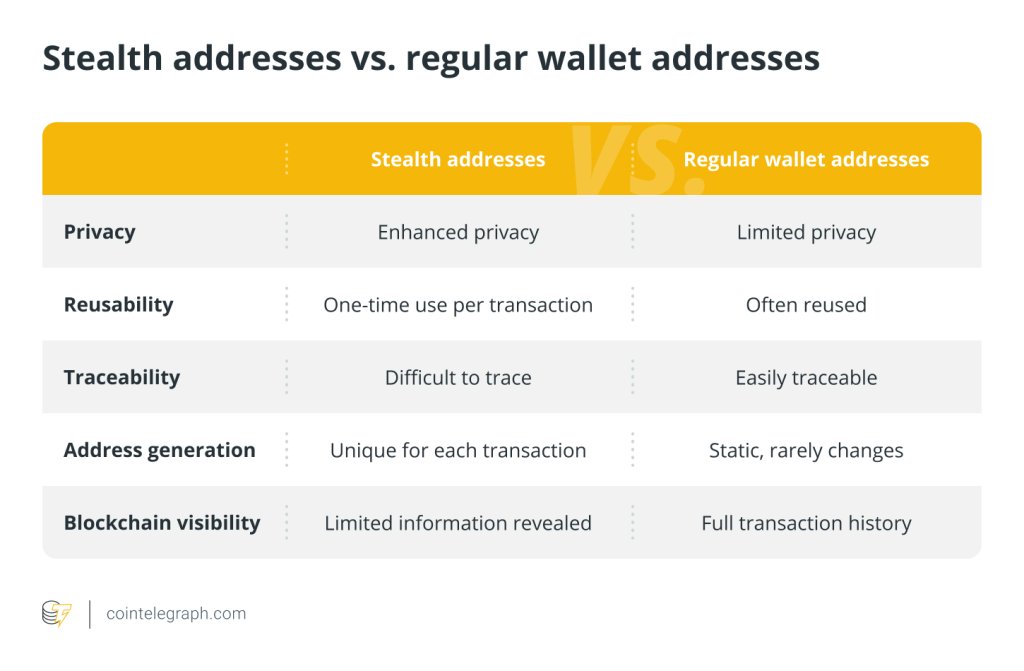
By creating a one-time address for each interaction, they anonymize operations and protect users’ identities from being linked to their blockchain activities. This quality is critical for various use cases where privacy is of utmost concern.
Stealth Addresses complexity
One of the main challenges is the complexity they introduce to the transaction processes. Users without technical knowledge might find it difficult to use Stealth Addresses, possibly leaving them more vulnerable.
As such, there is a need to create user-friendly interfaces and craft comprehensive educative content to allow even non-technical users to utilize Stealth Addresses effectively.
Transaction costs and Stealth Addresses
Another challenge is the increase in transaction costs linked to Stealth Addresses due to the requirement of publishing additional on-chain data for each transaction. For instance, the bare-bones nature of these addresses raises issues when it comes to transaction fees or ‘gas’ in Ethereum. As the Stealth Address contains only what the sender transferred, the recipient might not have enough Ethereum (ETH) to cover gas fees for subsequent transactions. These extra costs could hinder the widespread adoption of Stealth Addresses.
One way around this could be adding ETH from another wallet but that would create a publicly visible link, thus defeating the whole purpose of a Stealth Address. Some proposed solutions to this issue include making use of an advanced type of zero-knowledge proofs (ZK-SNARKs) or specialized transaction aggregators. Both options have their advantages, efficiencies, and trade-offs, and it’s crucial to consider them when integrating Stealth Addresses into an existing system.
Regulatory and audit challenges for Stealth Addresses
Lastly, Stealth Addresses could potentially hamper the efficiency of conventional blockchain analysis techniques used to detect illegal activities. To mitigate this, developing new, robust tools and methodologies is necessary.
Regulatory bodies could potentially see Stealth Addresses as a way to bypass anti-money laundering (AML) regulations or facilitate other illegal activities. Consequently, projects deploying Stealth Addresses may face scrutiny and resistance from regulatory authorities.
Use cases for Stealth Addresses
Stealth Addresses significantly enhance privacy across various scenarios, from crowdfunding campaign security to transaction anonymity on blockchain networks, notably within the Monero protocol. Let’s explore these use cases for Stealth Addresses and highlight their crucial role in ensuring transaction privacy, concealing identities, and promoting a more secure digital financial landscape.
Protecting identity in crowdfunding campaigns
Crowdfunding campaigns often accept cryptocurrencies due to their global nature and the simplicity of supporting them via digital wallets. However, exposing the wallet address of the receiver poses security risks as it opens up possibilities for tracking.
Stealth Addresses protect the privacy of receivers in such scenarios by generating unique addresses for each transaction, making it difficult for external observers to link transactions to individuals, thus preserving the identity of the campaign owner.
Increased network privacy
Stealth Addresses can enhance privacy features across various crypto protocols, not just limited to a single network. Given the public ledger system and pseudonymous nature of many cryptocurrencies, transaction details like the sender, receiver, and amount are typically visible to all.
By implementing Stealth Addresses, users of these protocols can obscure these details, enabling more private transactions across the board.
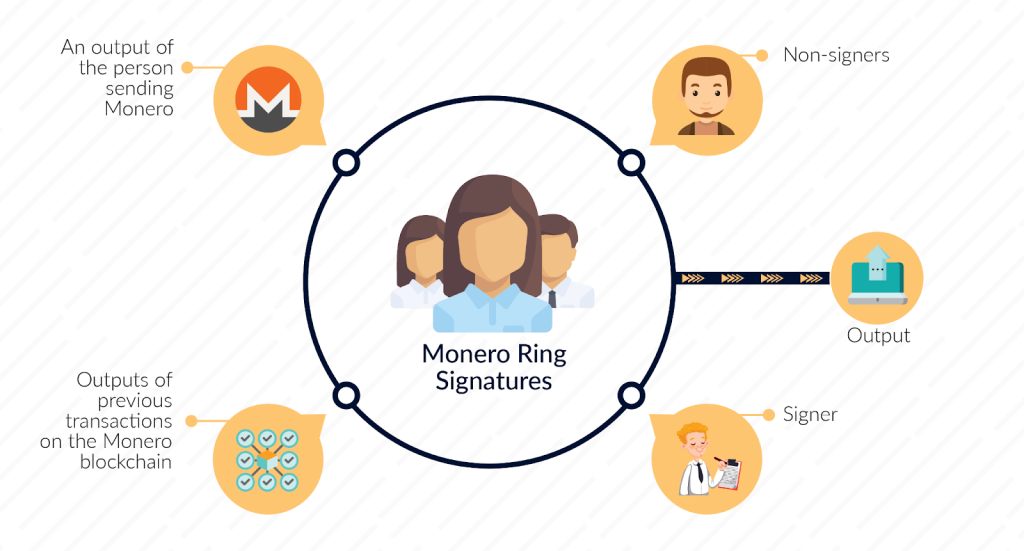
Monero: The Stealth Addresses protocol
Monero, a favorite among privacy enthusiasts, employs Stealth Addresses to ensure each transaction on its blockchain remains 100% untraceable. When a user sends XMR (Monero’s native cryptocurrency), the funds are directed to a Stealth Address associated with the receiver’s wallet.
Here, both sender and receiver identities remain concealed, as the transaction is “disguised” amongst several others thanks to the ring confidential transaction (RingCT) mechanism. Monero gives us a practical example of Stealth Addresses in real-world usage, enabling privacy-preserving transactions on its network.
Stealth Addresses, in essence, enhance the privacy capabilities of cryptocurrencies, allowing users to maintain anonymity in a world where the traceability of transactions is often probable, if not straightforward. As more and more industries recognize and adopt blockchain technology, timely developments like Stealth Addresses that prioritize user privacy will become increasingly essential.
Stealth Addresses and their future
As we stand on the brink of technological revolutions that promise to redefine the landscape of digital privacy and security, Stealth Addresses emerge as a beacon of hope and innovation. Let’s examine the future of Stealth Addresses, exploring their resilience against the anticipated challenges posed by quantum computing, their potential impact on EVM-based wallets, and their evolving implementation within the blockchain ecosystem.
Anticipating the advent of quantum computers
The advent and proliferation of quantum computers pose a potential threat to cryptographic systems, including Stealth Addresses. Quantum computing, by virtue of its computational power, could potentially decode cryptographic systems faster and more efficiently, leading to potential privacy breaches.
However, developers behind Stealth Addresses have recognized this emerging threat and are working towards creating “quantum-resistant” Stealth Addresses. These are designed to withstand attacks from quantum computers, continuing to provide a robust privacy solution for crypto transactions.
Implications for EVM-based Wallets
For EVM-compatible blockchains, one of the privacy concerns relates to the link between the sender and the recipient which is publicly visible on the ledger. In this respect, Stealth Addresses could have a significant impact. By generating a unique address for each transaction, Stealth Addresses could be a game-changer for EVM-based wallets, providing an added layer of privacy and security to Ethereum users.
Stealth Addresses implementation
The concept of Stealth Addresses got its start in the Bitcoin community, but more recently, its implementation got integrated into the Ethereum ecosystem as well. Developers are increasingly starting to experiment with implementing Stealth Addresses on Ethereum, using smart contracts. Ethereum offers an advantage over Bitcoin in this aspect, given that smart contracts allow for more complex transactions and provide the ability to generate Stealth Addresses without changing the base layer protocol.
In conclusion, while Stealth Addresses may currently seem like an advanced and perhaps niche privacy feature, we believe they have the potential to become mainstream in the not-too-distant future. The ongoing evolution and development in the crypto and blockchain space will undoubtedly continue to push the boundaries of what’s possible, and Stealth Addresses will undoubtedly be part of that journey.
Bringing it all together
Stealth Addresses, with their innovative approach to privacy, mark a significant advancement in blockchain technology. By enabling one-time, untraceable transaction addresses, they not only bolster the anonymity of blockchain interactions but also provide a promising platform for developing highly secure, privacy-preserving applications.
Nevertheless, the adoption of Stealth Addresses is not without its hurdles. Limited user understanding, higher transaction costs, and resilience against quantum threats are among the challenges that need addressing to ensure their extensive implementation and acceptance. As we step forward into a future where financial privacy could become increasingly vital, comprehending the power of dynamically concealed transaction identities given by Stealth Addresses will play a crucial role in shaping the landscape of monetary transactions.
In the grand scheme of things, Stealth Addresses embody a meaningful stride towards a world where the power of money management can truly belong to the people, without compromising the sanctity of their privacy. The precise nuances of this technology and its potential integrations are just beginning to ripple across the ecosystem—making it a fascinating theme to keep an eye on.
Remember, this evolving techscape demands an equal measure of openness to innovation and a keen eye on privacy—and Stealth Addresses, despite their challenges, appear to be a solid step towards balancing these crucial parameters. Here’s to a more private, secure transactional future!
Power-boost your project on Chainstack
- Discover how you can save thousands in infra costs every month with our unbeatable pricing on the most complete Web3 development platform.
- Input your workload and see how affordable Chainstack is compared to other RPC providers.
- Connect to Ethereum, Solana, BNB Smart Chain, Polygon, Arbitrum, Base, Optimism, Avalanche, TON, Ronin, zkSync Era, Starknet, Scroll, Aptos, Fantom, Cronos, Gnosis Chain, Klaytn, Moonbeam, Celo, Aurora, Oasis Sapphire, Polygon zkEVM, Bitcoin and Harmony mainnet or testnets through an interface designed to help you get the job done.
- To learn more about Chainstack, visit our Developer Portal or join our Discord server and Telegram group.
- Are you in need of testnet tokens? Request some from our faucets. Multi-chain faucet, Sepolia faucet, Holesky faucet, BNB faucet, zkSync faucet, Scroll faucet.
Have you already explored what you can achieve with Chainstack? Get started for free today.
 Ethereum
Ethereum Solana
Solana TON
TON Base
Base BNB Smart Chain
BNB Smart Chain Sui
Sui Unichain
Unichain Aptos
Aptos TRON
TRON Ronin
Ronin zkSync Era
zkSync Era Sonic
Sonic Polygon
Polygon Gnosis Chain
Gnosis Chain Scroll
Scroll Avalanche Subnets
Avalanche Subnets Polygon CDK
Polygon CDK Starknet Appchains
Starknet Appchains zkSync Hyperchains
zkSync Hyperchains