Demystifying Zero-Knowledge Proofs: The future of Web3 privacy

In the vast landscape of cryptography and blockchain technology, Zero-Knowledge Proofs (ZKPs) emerge as a beacon of privacy and security. Their concept, though born out of academically dense theories presented in 1985, have matured to significantly impact how we approach and solve modern-day privacy concerns.
As our world becomes increasingly interconnected through digital networks, privacy becomes both a luxury and a necessity. We conduct transactions, share sensitive information, and authenticate identities over networks teeming with potential threats. In such a landscape, how can we preserve our privacy while performing these crucial activities? ZKPs may hold the key. Let’s see why:
What are ZKPs?
ZKPs are not merely another cybersecurity model. Instead, they redefine how we perceive privacy in the digital realm. They allow for the novel act of confirming a statement’s truth without revealing any additional information – like proving you know a password without ever disclosing what it is. Such innovative applications make ZKPs a fascinating field of exploration and a tool to power our increasingly digital world.
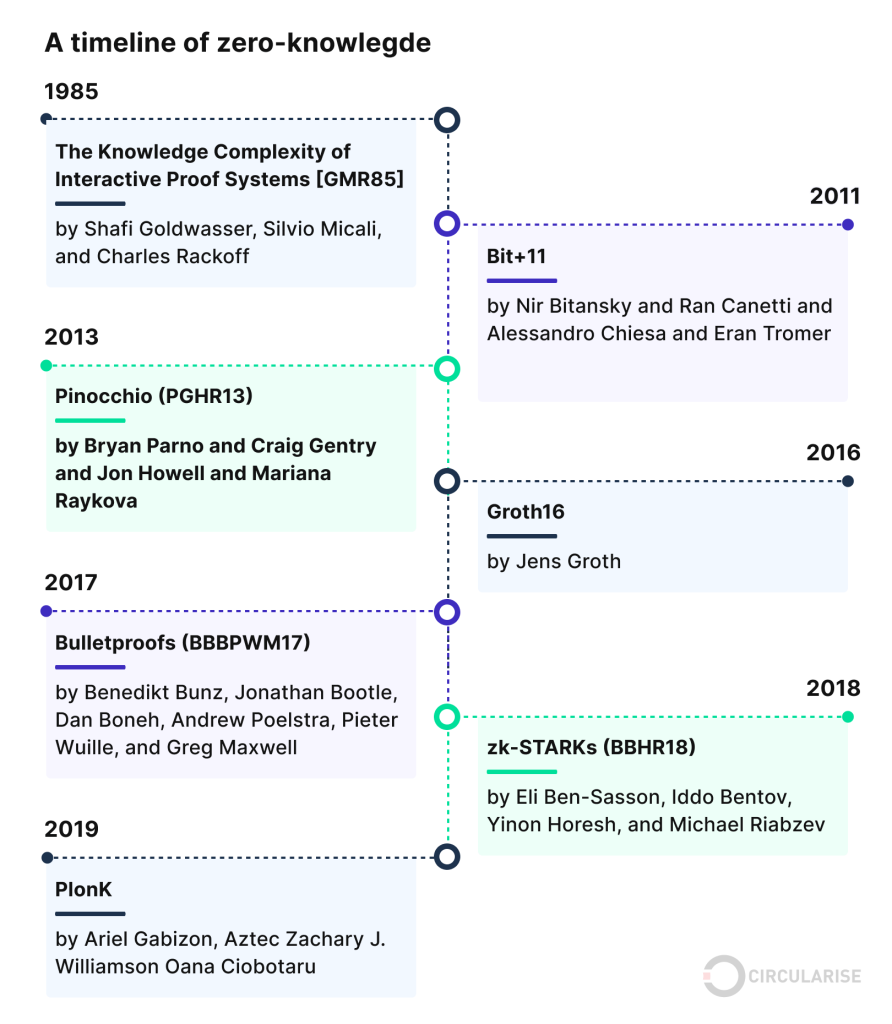
The concept of Zero-Knowledge Proofs was first introduced in a groundbreaking 1985 paper by Shafi Goldwasser, Silvio Micali, and Charles Rackoff. The initial revelation sparked a deluge of interest and subsequent research in the field of cryptography.
Over the past three decades, ZKPs have significantly evolved and have found valuable applications in various real-world scenarios, especially in the realm of blockchain technology. As we delve into the world of ZKPs, we begin to appreciate their strategic importance and potential in modern-day information sharing and privacy protection.
Comparing ZKPs and zero trust
It is essential to distinguish between ZKPs and “zero trust.” The latter is a cybersecurity model that treats every person and device as a potential threat, necessitating continuous authentication and authorization. On the other hand, ZKPs constitute a method that enables one party (the prover) to confirm the truth of a statement without revealing any information about the statement’s contents to another party (the verifier). Notably, ZKPs can function within a zero-trust framework, providing a secure mechanism for authentication without necessitating the exposure of personal details.
The role of ZKPs in preserving privacy
In an era where information is pivotal, preserving privacy has become more critical than ever before. Conventional methods of verifying claims, such as showcasing your passport or driver’s license, tend to expose personal information to third parties, increasing the vulnerability to potential hacks and identity theft. This is where ZKPs step in, eliminating the need to disclose information while still providing a proof of the claim’s validity. With ZKPs, it is possible to establish the truth of a statement without exposing any of the information required to validate it.
Understanding ZKPs
At the core of ZKPs are three fundamental criteria that they must satisfy: completeness, soundness, and zero knowledge.
Completeness ensures that if a statement is valid, the protocol will always return ‘true.’ This ensures the reliability of the verification process and instills confidence in the underlying system.
Soundness refers to the impossibility of fooling the system. If a statement is false, it is impossible for a prover to convince the verifier that it is true, enhancing the system’s integrity.
The final criterion, Zero-knowledge, guarantees that the verifier learns nothing about the statement beyond its validity or falsity. This means that the validation process does not reveal any additional or unnecessary information, thus protecting the system’s security.
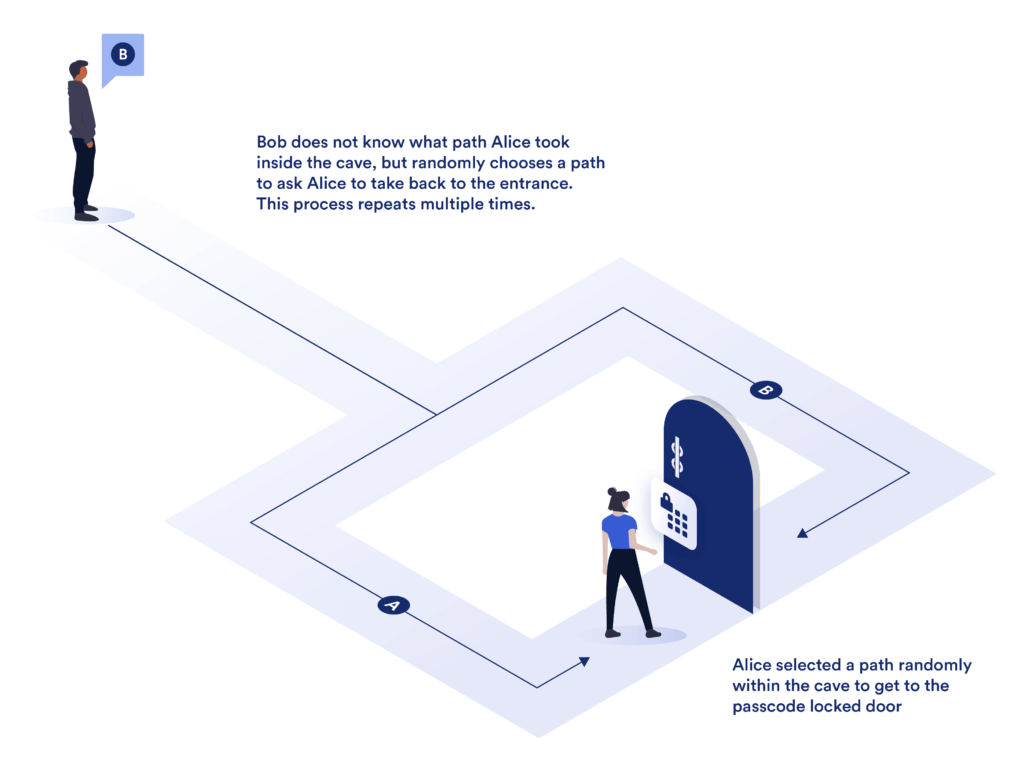
Understanding interactive vs. non-interactive ZKPs
ZKPs can be interactive or non-interactive, depending on the style of communication required.
Interactive ZKPs entail an ongoing, back-and-forth communication between the prover and verifier. This becomes akin to a game, where the verifier challenges the prover, who then provides responses that convince the verifier of the statement’s truth.
In contrast, non-interactive ZKPs demand only a single round of communication—the prover generates and sends the proof to the verifier. The verifier can then independently authenticate the proof using a shared key and a verification algorithm. Notably, non-interactive ZKPs are more efficient and reduce the potential for errors, as they eliminate the need for continuous interaction.
Types of ZKPs
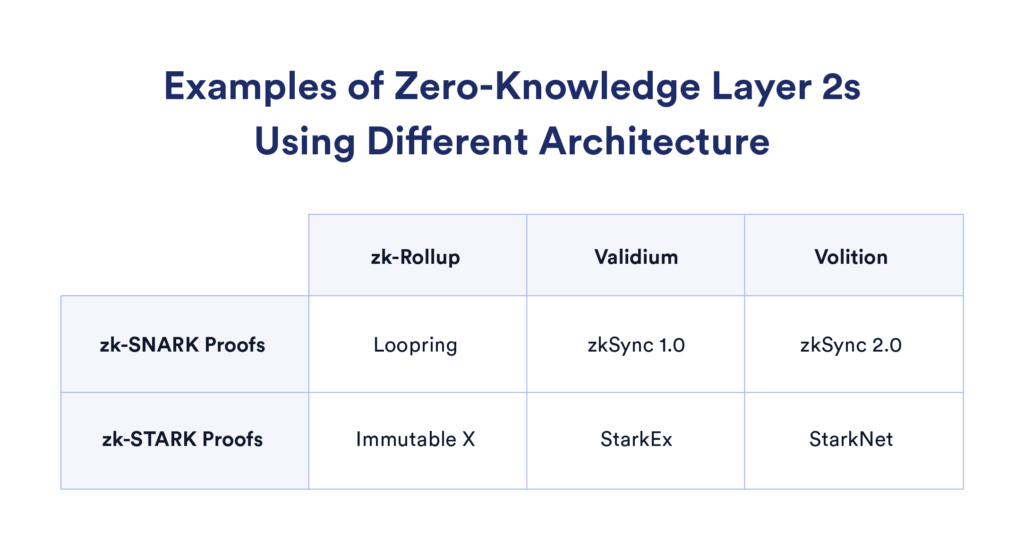
Several variants of ZKPs have emerged over the years, each tailored to specific applications or optimized for certain challenges. Notable among these are ZK-SNARKs (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge), ZK-STARKs (Zero-Knowledge Scalable Transparent Argument of Knowledge), PLONKs, and Bulletproofs.
ZK-SNARKs involve a succinct proof and verification process, requiring little communication between the prover and verifier and enabling efficient proof verification. However, ZK-SNARKs necessitate a trusted setup, potentially introducing vulnerabilities if this process is compromised.
In contrast, ZK-STARKs sacrifice compactness for transparency, removing the need for a trusted initial setup. They are also more scalable than ZK-SNARKs, able to handle larger computational statements while maintaining relative efficiency.
At the core of both PLONKs and Bulletproofs is the commitment to reduce computational and proof size requirements, making these types of ZKPs highly efficient.
Benefits and use cases of ZKPs types
Each type of ZKP comes with its benefits and use-cases, decided by their unique characteristics.
- ZK-SNARKs are highly efficient, requiring shorter proofs and less computation, making them ideal for scalability and for applications demanding quick proof and verification.
- ZK-STARKs, on the other hand, offer greater security and universal verifiability, as they do not rely on a trusted setup. This feature makes ZK-STARKs suitable for applications that prioritize security and transparency over efficiency.
- PLONKs generalize the concept used in ZK-SNARKs, resulting in a simpler protocol and broadening their use-cases.
- Meanwhile, Bulletproofs are designed to enable efficient confidential transactions in cryptocurrencies.
ZKPs applications in a Web3 context
Enhancing privacy and transparency
The marriage between blockchain networks and ZKPs has opened up a world of possibilities for enhancing both privacy and transparency in digital transactions. By utilizing ZKPs, blockchain users can prove possession of a specific piece of knowledge or fulfilment of a particular condition without revealing any details about it. This provides a layer of privacy, shielding information from other users on the network, while maintaining the transparency characteristic of blockchain technology.
For instance, consider individuals performing a transaction on a public blockchain. Through ZKPs, these individuals can anonymously prove to the rest of the network that they have enough cryptocurrency for a transaction, without showing exactly how much they own. This protects user privacy while keeping the transaction open and transparent for anyone on the blockchain to verify.
Anonymous payments using ZKPs
Anonymity of payments is a vital use-case of ZKPs in blockchain networks. ZKPs can mask transaction details, camouflaging the sender’s, recipient’s, and transaction amount’s identities. This ensures financial privacy, something highly valued in crypto-economics. Coins like Zcash use ZK-SNARKs to enable private transactions.
Identity protection and authentication simplified
Beyond maintaining financial privacy, ZKPs play an essential role in safeguarding digital identities on blockchain networks. By deploying ZKPs, individuals can verify their identity or authenticate themselves without revealing sensitive details. Taking it a step further, ZKPs can simplify authentication for online services, eliminating the need for users to remember complex passwords or provide personal information.
The Future of ZKPs
Addressing the challenges and drawbacks of ZKPs
While ZKPs have a lot of promising applications, they are not without drawbacks. Some of these challenges include high hardware costs for generating proofs, verification costs that can become prohibitively high for large-scale applications, and trust assumptions in certain types of ZKPs like ZK-SNARKs, which could potentially be exploited.
Moreover, the imminent threat posed by quantum computing can potentially crack current cryptographic practices, including ZKPs. Thankfully, research is being pursued vigorously in the area of quantum-resistant cryptography that could also secure ZKPs against quantum attacks.
Ongoing research and development in ZKPs
The cryptographic community is heavily focused on tackling these problems and furthering the application of ZKPs. Ongoing research and development are aimed at reducing hardware and validation costs, eliminating trust assumptions, and designing quantum-resistant cryptographic practices.
It’s a fascinating field, with the full potential of ZKPs yet to be harnessed. With privacy being an increasingly important factor in digital communication and transactions, it is likely that we’ll see ZKPs being integrated into more and more systems.
Exploring the future implications of ZKPs
The increasing digitization of our world promises a future where ZKPs could be more widely used. In the field of decentralized identity, for instance, ZKPs can provide a secure and reliable way for people to prove aspects of their identity without needing to reveal any unnecessary information.
From securing our digital identities to providing greater privacy in blockchain transactions, the potential applications of ZKPs are far-reaching and exciting. As research and understanding of ZKP continue to evolve, the future of ZKPs seems more promising than ever.
Bringing it all together
Zero-Knowledge Proofs are a revolutionary technology that has significantly impacted the way we confront the issue of privacy in the digital age. With their ability to confirm a statement’s truth without exposing any additional information, ZKPs have found essential applications spanning from Blockchain transactions to digital identity verification.
However, as with any innovative technology, ZKPs come with their set of challenges. These include high hardware requirements, expensive verification costs, trust assumptions, and potential threats from quantum computing. Yet, the community is working persistently towards overcoming these issues, and ongoing research shows promising possibilities for the future of ZKPs.
In our quest for more secure and private digital interactions, ZKPs offer a beacon of hope. As we continue to innovate and break new ground in this field, ZKPs will undoubtedly play a pivotal role in shaping our digital future, one where privacy is a right, not a privilege, and transparency can coexist with confidentiality.
As we conclude this deep dive into ZKPs, let’s remember that while the depth of these concepts can be overwhelming, the value they provide to our increasing digital interactions is immeasurable. With ZKPs, we are one step closer to a world where our digital selves are not just blindly secure but are also to be devoid of unnecessary exposure.
Power-boost your project on Chainstack
- Discover how you can save thousands in infra costs every month with our unbeatable pricing on the most complete Web3 development platform.
- Input your workload and see how affordable Chainstack is compared to other RPC providers.
- Connect to Ethereum, Solana, BNB Smart Chain, Polygon, Arbitrum, Base, Optimism, Avalanche, TON, Ronin, zkSync Era, Starknet, Scroll, Aptos, Fantom, Cronos, Gnosis Chain, Klaytn, Moonbeam, Celo, Aurora, Oasis Sapphire, Polygon zkEVM, Bitcoin and Harmony mainnet or testnets through an interface designed to help you get the job done.
- To learn more about Chainstack, visit our Developer Portal or join our Discord server and Telegram group.
- Are you in need of testnet tokens? Request some from our faucets. Multi-chain faucet, Sepolia faucet, Holesky faucet, BNB faucet, zkSync faucet, Scroll faucet.
Have you already explored what you can achieve with Chainstack? Get started for free today.
 Ethereum
Ethereum Solana
Solana TON
TON Base
Base BNB Smart Chain
BNB Smart Chain Sui
Sui Unichain
Unichain Aptos
Aptos TRON
TRON Ronin
Ronin zkSync Era
zkSync Era Sonic
Sonic Polygon
Polygon Gnosis Chain
Gnosis Chain Scroll
Scroll Avalanche Subnets
Avalanche Subnets Polygon CDK
Polygon CDK Starknet Appchains
Starknet Appchains zkSync Hyperchains
zkSync Hyperchains