Enterprise Solana infrastructure: What matters in 2026

Introduction: TPS vs RPC Performance in Enterprise Solana
When enterprise teams evaluate Solana, they often focus on headline metrics like theoretical throughput. But applications never interact with network TPS directly. What actually defines production performance is how reliably RPC infrastructure delivers Solana data to applications under real-world load.
This distinction matters in 2026. Solana consistently produces blocks every ~400 milliseconds, yet many production systems still experience hundreds of milliseconds—or more—of RPC latency under peak conditions. For payment systems, trading platforms, and compliance-heavy deployments, these delays directly impact user experience, settlement times, and operational reliability.
This article explains what enterprise-grade Solana infrastructure really means today, why network throughput alone says little about application performance, and which RPC characteristics determine whether a Solana deployment succeeds in production.
Part 1: Why enterprise Solana infrastructure is not about TPS
Enterprises evaluating Solana often anchor on headline metrics: 400 ms block times and thousands of transactions per second. But applications never interact with network throughput directly. What defines real production performance is how quickly and reliably RPC infrastructure delivers that data to applications.
Solana can sustain 1,500–4,000 TPS and produce blocks every ~400 milliseconds, yet many production systems still experience 500 ms to 2+ seconds of RPC latency during peak load. The blockchain performs as expected — the bottleneck appears at the infrastructure layer.
Network TPS measures how many transactions validators can process across the distributed network. RPC latency measures how fast your application can read and write that data through an API endpoint. These are entirely separate performance characteristics, and confusing them leads to broken production assumptions.
Consider a payment processor handling 10,000–50,000 USDC transfers per day. Throughput requirements are modest, but each payment flow requires multiple RPC calls: balance checks, transaction submission, confirmation tracking, and state updates. If each call takes 500 ms instead of 50 ms, end-to-end settlement time quickly exceeds user and SLA expectations — despite Solana confirming transactions almost instantly.
The same issue appears in real-time dashboards. Portfolio and trading interfaces rely on continuous RPC queries for balances and program state. When RPC latency spikes, users see stale data and make decisions on outdated information. Solana’s block time remains unchanged, but application experience degrades.
In enterprise deployments, RPC latency — not network TPS — determines whether Solana feels fast or unusable in production.
What to evaluate in enterprise Solana infrastructure
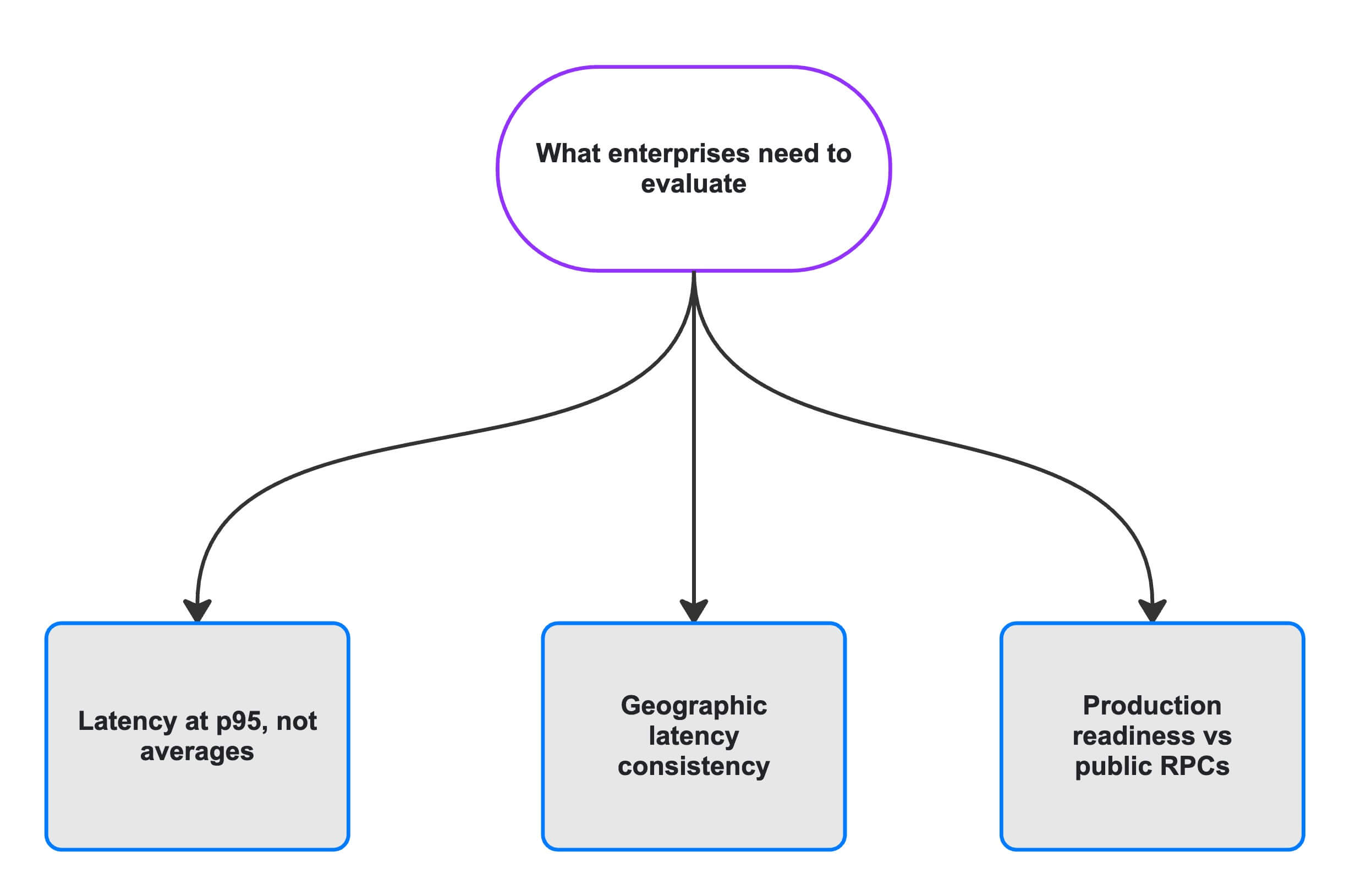
First, demand p95 latency guarantees, not average latency. A provider claiming “average 50ms latency” might deliver 20ms most of the time but spike to 300ms for five percent of requests. That five percent represents every twentieth user experiencing degraded interface performance.
Second, geographic distribution matters enormously for global applications. An RPC endpoint in US-East might serve New York with 20ms latency but deliver 200ms to Singapore. Production infrastructure requires regional endpoints in North America, Europe, and Asia-Pacific with automatic traffic routing.
Third, understand the difference between public and production RPC endpoints. Solana’s public RPC endpoints implement rate limiting at 40 requests per 10 seconds, and official documentation explicitly states these endpoints are “not intended for production applications.” Applications attempting to run production workloads against public endpoints will hit rate limits immediately and experience unpredictable throttling.
Part 2: Predictable performance in enterprise Solana infrastructure
Enterprise systems value consistency over peak benchmarks. An RPC endpoint delivering 50 ms latency 99.99% of the time is more valuable than one that occasionally hits 20 ms but frequently degrades to 500 ms under load. Unfortunately, many RPC providers optimize for best-case benchmarks rather than worst-case production behavior.
In real-world conditions, infrastructure stress rarely comes from your own application. During high-traffic events—such as major NFT mints or ecosystem launches—shared RPC infrastructure often experiences elevated latency and slot lag, even while the Solana network itself continues producing blocks every ~400 milliseconds. Applications fail not because Solana slows down, but because shared infrastructure becomes saturated.
This is the classic noisy-neighbor problem. On shared RPC nodes, your requests compete with other customers’ workloads for CPU, memory, and network bandwidth. Expensive queries—such as large getProgramAccounts scans—can temporarily degrade performance for every tenant on the same node. From an application perspective, this manifests as sudden latency spikes, timeouts, or intermittent 429 errors.
Unpredictability is compounded by hidden quotas. Providers frequently advertise “unlimited requests,” yet enforce undocumented throttles that surface only under real traffic. Capacity planning becomes impossible when limits are discovered reactively in production rather than defined contractually in advance.
For enterprise deployments, predictable performance requires eliminating shared contention entirely. Dedicated infrastructure, explicit RPS guarantees, and SLA-backed latency targets are not optimizations—they are prerequisites for running Solana applications in production at scale.
Core requirements for enterprise Solana infrastructure
| Dedicated nodes | Exclusive infrastructure with no shared tenancy to eliminate noisy-neighbor effects and guarantee predictable performance under load. |
| Guaranteed RPS tiers with SLA backing | Clearly defined RPS tiers and latency targets with contractual SLAs and financial penalties for violations—not “best-effort” commitments. |
| 99.99% uptime | Availability guarantees limiting downtime to minutes per month, documented and backed by financially meaningful SLAs. |
| Transparent pricing | Complete Solana history from genesis with low-latency queries for compliance, audits, and long-range analytics—without artificial retention limits. |
Part 3: Real-Time and Historical Data Together
Enterprise applications require two data workloads simultaneously: low-latency access to current state and fast queries over long-term history. Most RPC architectures are optimized for one—but not both.
Real-time access powers user-facing systems. Payment flows, dashboards, and trading interfaces depend on immediate balance checks and confirmation tracking. With Solana producing blocks every ~400 ms, these workloads demand consistently low RPC latency to avoid stale data and broken UX.
Historical access supports compliance and analytics. Audits and reporting often require reconstructing account activity months or years in the past. With tens of billions of transactions processed annually, historical query performance has become a core infrastructure requirement—not a niche feature.
The architectural tension is clear. Real-time RPC nodes prune historical data aggressively, often retaining only ~30 days. Archive nodes store full history but typically serve older data much more slowly due to storage constraints. For enterprise systems, switching infrastructure modes depending on the task is not viable.
Production-grade Solana infrastructure must deliver low-latency real-time access while supporting fast, reliable queries across the full blockchain history—from genesis onward—without performance trade-offs.
What enterprise Solana deployments require
Archive nodes should maintain sub-200 millisecond query times even when accessing historical data from early blocks. This requires significant engineering investment in storage architecture, caching strategies, and query optimization.
Block history retention from genesis forward represents table-stakes for compliance-heavy industries. Financial services regulations frequently mandate seven-year data retention. When evaluating Solana infrastructure, verify that providers can serve data from any point in the blockchain’s history—from March 2020 genesis forward—without gaps.
Efficient getProgramAccounts queries on historical state are essential for reconstructing portfolio holdings at specific points in time or generating historical reports. Well-engineered archive nodes use indexing strategies and caching to make these queries practical.
Consider the stablecoin issuer use case. Solana now hosts over $15 billion in stablecoin supply. Major institutions like Visa settle billions in payment volume on Solana. During normal operations, issuers need real-time balance checks to process transfers instantly. But when regulators request an audit, those same systems must reconstruct every transaction for the past six months or longer. If infrastructure can only serve real-time data efficiently, the audit process becomes manually intensive. If it only serves historical data slowly, normal operations suffer. The only acceptable solution is infrastructure that excels at both simultaneously.
Part 4: Security and isolation in Solana enterprise
Shared infrastructure represents unacceptable security and compliance risk for most enterprise deployments. The surface area for attack and lack of meaningful access controls in shared RPC environments create numerous vulnerabilities that become critical when handling institutional-scale value flows.
Public RPC endpoints expose several critical risks. First, they provide no IP allowlisting capability. Your production payment system shares the same API endpoint anyone on the internet can access. Solana’s public RPC endpoints document rate limits of 40 requests per 10 seconds explicitly because they must protect against arbitrary internet traffic. There’s no way to ensure only your infrastructure can reach the RPC node. From a security architecture perspective, this is equivalent to running a database with no firewall rules.
Second, public endpoints create enormous attack surfaces for denial of service. Because anyone can reach the endpoint, attackers can flood it with traffic. Even if the provider implements rate limiting, those limits apply uniformly across all customers. A sustained attack against shared infrastructure degrades performance for every customer simultaneously. This risk is particularly acute given the billions of dollars in institutional value now flowing through Solana.
Third, shared rate limits provide no isolation between customers. When one customer launches a feature generating unexpected traffic, all customers share the pain of increased latency and potential throttling. During 2024-2025, multiple documented incidents showed shared RPC infrastructure degrading across all customers during high-traffic events, even though the underlying Solana network maintained performance.
Enterprise security requirements
| IP allowlisting | Strict source IP controls to ensure only authorized environments can access RPC infrastructure. |
| Dedicated infrastructure | Exclusive RPC nodes with full resource isolation to eliminate shared-risk exposure and noisy-neighbor effects. |
| Private endpoints | RPC endpoints reachable only via private networking (VPC peering), not the public internet. |
| SOC 2 Type II certification | SOC 2 Type II–certified operations with request-level logs retained to meet regulatory audit requirements. |
Part 5: Real Enterprise Use Cases
Three categories of enterprise deployments stress different aspects of RPC infrastructure, and 2025-2026 adoption demonstrates these requirements aren’t theoretical.
Payment processor workloads (Visa, stablecoin settlement)
Visa processes approximately $3.5 billion in annualized USDC settlement volume on Solana. Payment flows are latency-sensitive and multi-step: balance validation, transaction submission, confirmation tracking, and reconciliation. Even small increases in RPC latency compound across these steps and directly impact settlement SLAs.
For these systems, WebSocket reliability is critical. Push-based transaction confirmations reduce polling overhead and latency, but unstable connections or missed events introduce reconciliation risk. When settling institutional payment volume, dropped confirmations translate into operational incidents, not just degraded UX.
Historical access is equally important. Payment disputes and regulatory reviews often occur weeks or months after execution. Infrastructure limited to short-term data retention forces operators to maintain parallel off-chain databases, increasing complexity and audit risk.
Institutional Solana use cases and regulated assets (JPMorgan, tokenized securities)
In 2025, JPMorgan issued $50 million in tokenized commercial paper on Solana, demonstrating that regulated securities are now settling on the network. These workflows impose strict compliance requirements: complete transaction traceability, long-term data retention, and verifiable auditability.
Auditors may request reconstruction of account state at specific historical points, spanning fiscal quarters or entire years. Infrastructure that cannot efficiently serve historical state queries at scale turns audits into manual, time-consuming processes. For regulated institutions, full archive access from genesis forward is non-negotiable.
Enterprise Solana infrastructure for stablecoins (Circle, PayPal)
Major stablecoin issuers operate dual workloads. Day-to-day operations require low-latency real-time access to process transfers, manage liquidity, and monitor circulating supply. At the same time, treasury and compliance teams require fast historical queries to reconcile issuance, redemptions, and reserve backing over long time horizons.

For example, PayPal’s PYUSD, issued on Solana, operates across multiple chains but has seen sustained transaction activity on Solana since mid-2025. Managing this activity at scale requires infrastructure capable of serving both real-time operational queries and historical analytics without switching systems or degrading performance.
To learn more about stablecoins on Solana, see our detailed overview here: Stablecoins on Solana in 2026: Growth, adoption, and usage
Part 6: Evaluating Solana RPC Providers in 2026
Enterprise teams should evaluate Solana RPC providers based on measurable production behavior—not marketing benchmarks. The following criteria determine whether an RPC provider can support institutional workloads at scale.
Performance under real load
Demand p95 latency metrics, not averages. Providers should demonstrate stable latency during peak network activity, including ecosystem-wide traffic spikes. Historical incidents have shown some providers maintaining low average latency while p95 and p99 degraded beyond one second under load.
Throughput and throttling behavior
Verify whether the provider throttles requests during congestion. Shared infrastructure frequently enforces undocumented limits that surface only under real traffic. Enterprise deployments require clearly defined RPS tiers with contractual guarantees—not best-effort rate limiting.
Data availability and retention
Confirm full Solana history retention from March 2020 genesis onward. Test historical queries directly and compare latency against real-time state queries. Archive access should not be orders of magnitude slower or monetized as a premium add-on.
Infrastructure isolation
Shared RPC nodes are insufficient for production. Require dedicated infrastructure with exclusive access to compute and networking resources. True isolation eliminates noisy-neighbor effects and enables predictable capacity planning.
Reliability and uptime
Request documented uptime statistics covering the past 12 months, including both planned and unplanned outages. 99.99% uptime SLAs should be backed by meaningful financial penalties, not symbolic service credits.
Pricing predictability
Avoid opaque pricing models based on variable compute units. Flat per-request pricing or clearly defined RPS tiers enable accurate budgeting and prevent cost surprises as workloads scale.
In 2026, the difference between hobbyist and enterprise-grade Solana infrastructure is not theoretical performance. It is the ability to deliver consistent latency, predictable throughput, complete data access, and contractual reliability under real production conditions.
Checklist: Enterprise Solana infrastructure requirements
| Requirement | Why it matters for enterprise |
|---|---|
| P95 latency SLAs | Average latency hides spikes. Enterprise systems fail on tail latency, not benchmarks. |
| Dedicated infrastructure | Shared nodes introduce noisy-neighbor risk and unpredictable degradation under load. |
| Full archive access included | Compliance and audits require genesis-to-present data without add-ons or retention limits. |
| SOC 2 Type II coverage | Certification must apply to the actual RPC infrastructure, not adjacent services. |
| 99.99% uptime guarantees | Downtime directly impacts settlement SLAs and regulatory obligations. |
| Predictable pricing | Flat pricing or clear RPS tiers enable budgeting; compute units obscure real costs. |
Conclusion: Infrastructure determines enterprise outcomes
Solana has proven its capabilities as a high-performance blockchain. It consistently produces blocks every ~400 milliseconds, sustains thousands of transactions per second, and now settles billions of dollars in institutional value—from stablecoin payments to tokenized securities.
But enterprise applications never interact with Solana directly. They interact with RPC infrastructure.
In production, application performance is defined not by network throughput, but by RPC latency under load, data availability, security guarantees, and operational predictability. Many teams discover this distinction too late—after deployments encounter latency spikes, throttling, incomplete historical data, or compliance gaps.
By 2026, enterprise requirements are clear. Production Solana infrastructure must deliver:
- predictable p95 latency, not best-case benchmarks
- dedicated, isolated infrastructure without shared-risk exposure
- full historical data access from genesis onward
- security controls aligned with regulated environments
- pricing models that remain stable as workloads scale
The question enterprise teams should ask is no longer “Is Solana fast enough?”
The answer is unequivocally yes.
The real question is whether your infrastructure provider can consistently deliver Solana’s performance to your application, across real-world traffic, regulatory scrutiny, and long-term growth. That decision—not blockchain choice—ultimately determines whether an enterprise Solana deployment succeeds in production.
Chainstack’s enterprise approach
Chainstack’s Solana infrastructure is designed to meet the enterprise requirements outlined above. The platform provides dedicated RPC nodes with full resource isolation, eliminating noisy-neighbor effects common in shared environments. 99.99% uptime SLAs, backed by financial penalties, ensure availability aligned with payment and settlement workloads.
Global deployments are supported through geographically distributed endpoints across the US, Europe, and Asia-Pacific, delivering consistently low p95 latency for user-facing applications. Full archive access from genesis is included by default, enabling compliance, audits, and long-term analytics without separate data pipelines or retention limits.
Security controls are independently validated through SOC 2 Type II certification, while flat per-request pricing removes cost unpredictability associated with variable compute-unit models. Together, these design choices allow enterprise teams to operate Solana workloads with predictable performance, security, and cost at production scale.
Start for free, connect your app to a reliable Solana RPC endpoint, and experience how easy it is to build and scale on Solana with Chainstack – one of the best RPC providers.
FAQ
Network TPS measures how many transactions the blockchain can process. RPC latency defines how fast applications can read and write that data. Enterprise failures usually occur at the RPC layer, not the network layer.
Yes. Dedicated nodes eliminate noisy-neighbor effects, enable predictable performance, and allow SLA-backed guarantees that shared infrastructure cannot provide.
P95 latency shows how slow the slowest 5% of requests are. Averages hide spikes that directly degrade user experience and break enterprise SLAs.
No. Public endpoints are rate-limited, offer no SLA, retain limited history, and are explicitly documented as not intended for production use.
Enterprise-grade Solana infrastructure must scale predictably without performance degradation. This requires pre-defined capacity planning, dedicated resources, and the ability to increase RPS limits and node capacity without migrating endpoints or re-architecting applications. Scaling should be operationally transparent and contractually defined, not reactive or best-effort.
Yes. Chainstack offers an Enterprise plan for Solana infrastructure designed for production and regulated workloads. The Enterprise plan includes dedicated RPC nodes with full isolation, SLA-backed uptime guarantees, predefined RPS tiers, private networking options, and full archive access from genesis. The plan is built to support predictable performance, security, and cost at enterprise scale.
 Ethereum
Ethereum Solana
Solana Hyperliquid
Hyperliquid Base
Base BNB Smart Chain
BNB Smart Chain Monad
Monad Aptos
Aptos TRON
TRON Ronin
Ronin zkSync Era
zkSync Era Sonic
Sonic Polygon
Polygon Unichain
Unichain Gnosis Chain
Gnosis Chain Sui
Sui Avalanche Subnets
Avalanche Subnets Polygon CDK
Polygon CDK Starknet Appchains
Starknet Appchains zkSync Hyperchains
zkSync Hyperchains